![]()
(JVN#14876762, JVNDB-2014-000017, CVE-2014-0050)
Last Updated: February 19, 2014
HIRT reports the vulnerabilities to JVN in line with the framework of vulnerability handling - Information Security Early Warning Partnership.
Apache Commons FileUpload contains a denial-of-service (DoS) vulnerability.
Base Metrics: 5.0
Access Vector: Network
Access Complexity: Low
Authentication: None
Confidentiality Impact: None
Integrity Impact: None
Availability Impact: Partial
Temporal Metrics 3.9 (February 12, 2014)
Exploitablity: Proof of concept code
Remediation Level: Official fix
Report Confidence: Confirmed
+ Apache Commons FileUpload 1.0 to 1.3
+ Apache Tomcat 8.0.0-RC1 to 8.0.1
+ Apache Tomcat 7.0.0 to 7.0.50
+ Products that use Apache Commons FileUpload
Apache Tomcat 7 and Apache Tomcat 8 use a packaged renamed copy of Apache Commons FileUpload to implement the requirement of the Servlet 3.0 and later specifications to support the processing of mime-multipart requests. Tomcat 7 and 8 are therefore affected by this issue. While Tomcat 6 uses Commons FileUpload as part of the Manager application, access to that functionality is limited to authenticated administrators.
Processing a malformed HTTP request may cause the condition that the target system does not respond.
Update the Software
This issue was reported responsibly to the Apache Software Foundation via JPCERT/CC (Information Security Early Warning Partnership) but an error in addressing an e-mail led to the unintended early disclosure of this issue [*1]. Apache Software Foundation decided to publish the Security advisory as soon as possible [*2]. Also JPCERT/CC (coordination body), IPA (receipt body) and HIRT (discoverer) coordinated the public release (February 10, 2014) at JVN.
[2013-11-21] Confirmation of this vulnerability in Apache Commons FileUpload.
[2013-12-02] Vulnerability reported JVN in line with the Information Security Early Warning Partnership (Figure 1).
[2013-12-04] Receiving questions of "reproduction of the vulnerable condition" and "technical detail" from IPA (receipt body).
[2013-12-06] Sending the answer of "reproduction of the vulnerable condition" to IPA (receipt body).
[2013-12-09] Sending the answer of "technical detail" to IPA (receipt body).
[2013-12-25] Acceptance of this vulnerability reporting by IPA (receipt body).
[2014-01-09] Receiving an initial date in reckoning of this vulnerability reporting from IPA (receipt body).
[2014-02-06 01:45+00:00] cc'd vulnerability related information to org.apache.commons.dev [*1].
[2014-02-06 11:37+00:00] Security advisory public by Apache Software Foundation [*2].
[2014-02-07] Coordination of public release at JVN with JPCERT/CC (coordination body) and IPA (receipt body).
[2014-02-10] Public release at JVN [*3].
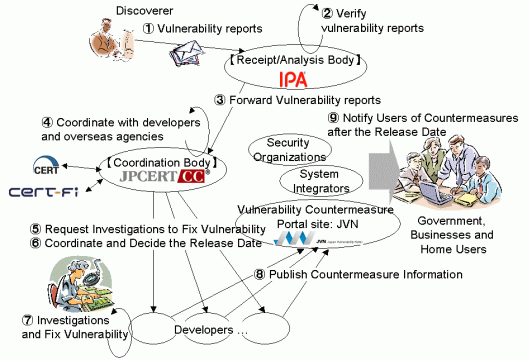
Figure 1. Framework overview of the Information Security Early Warning Partnership.
Masato Terada (HIRT), Akiko Numata (HIRT) and Naoko Ohnishi (HIRT)