![]()
(VU#252743, CVE-2014-6271, CVE-2014-7169)
Last Updated: October 7, 2014
GNU Bourne-Again Shell (Bash) contains a vulnerability that could allow an attacker to remotely execute shell commands by attaching malicious code in environment variables used by the operating system. This vulnerability is commonly referred to as "Shellshock".
September 24, 2014
GNU Bash vulnerability (CVE-2014-6271) in environment variables parsing was disclosed to the public.
Security update for GNU Bash vulnerability (CVE-2014-6271) has been released for most major Linux distributions.
September 25, 2014
GNU Bash Incomplete Fix Remote Code Execution Vulnerability (CVE-2014-7169) was disclosed to the public.
September 26, 2014
Security update for GNU Bash vulnerability (CVE-2014-7169) has been released for most major Linux distributions.
Also, Red Hat reported "Out of Bounds Memory Access Denial of Service Vulnerability (CVE-2014-7186)" and "Off-By-One Error Denial of Service Vulnerability (CVE-2014-7187)".
September 27, 2014
GNU Bash Incomplete Fix Remote Code Execution Vulnerability (CVE-2014-6277 and CVE-2014-6278) was disclosed to the public.
CVE-2014-6271: GNU Bash Remote Code Execution Vulnerability
CVE-2014-7169: GNU Bash Incomplete Fix Remote Code Execution Vulnerability
CVE-2014-7186: Out of Bounds Memory Access Denial of Service Vulnerability
CVE-2014-7187: Off-By-One Error Denial of Service Vulnerability
CVE-2014-6277: GNU Bash Incomplete Fix Remote Code Execution Vulnerability
CVE-2014-6278: GNU Bash Incomplete Fix Remote Code Execution Vulnerability
Base Metrics: 10.0
Access Vector: Network
Access Complexity: Low
Authentication: None
Confidentiality Impact: Complete
Integrity Impact: Complete
Availability Impact: Complete
Temporal Metrics 8.7 (September 27, 2014)
Exploitablity: High
Remediation Level: Official fix
Report Confidence: Confirmed
+ GNU Bash through 4.3
+ Linux, BSD, and UNIX distributions that use GNU Bash
+ Hitachi Products that use GNU Bash
By attacking a service that uses a vulnerable version of GNU Bash, a remote, unauthenticated attacker may be able to execute shell commands by attaching malicious code in environment variables used by the operating system.
Web application
CGI scripts are likely affected by this issue: when a CGI script is run by the web server, it uses environment variables to pass data to the script.
Secure Shell (SSH)
This issue can be used to execute any command to bypass the restricted command control.
DHCP client
DHCP client uses various environment variables and runs Bash to configure the network interface.
Connecting to a malicious DHCP server could allow an attacker to remotely execute arbitrary commands.
Mail server
qmail uses various environment variables to refer the value of mail from: and rcpt to:.
This can be used to execute arbitrary commands by specially crafted environment variables.
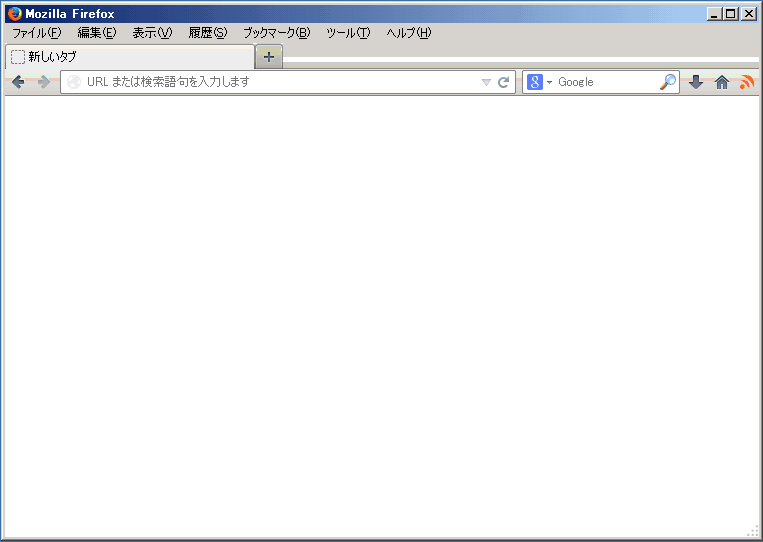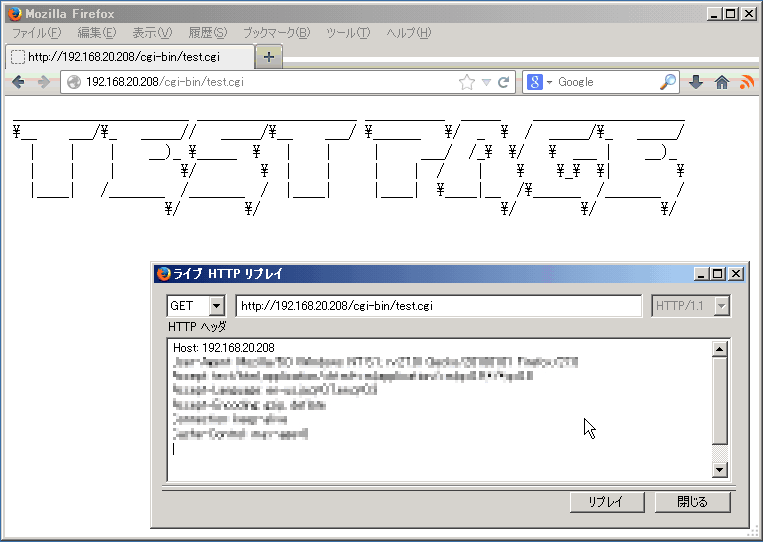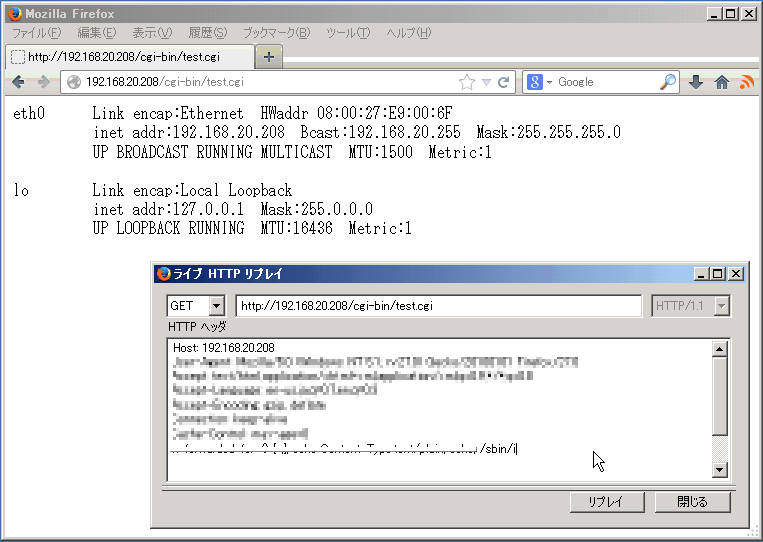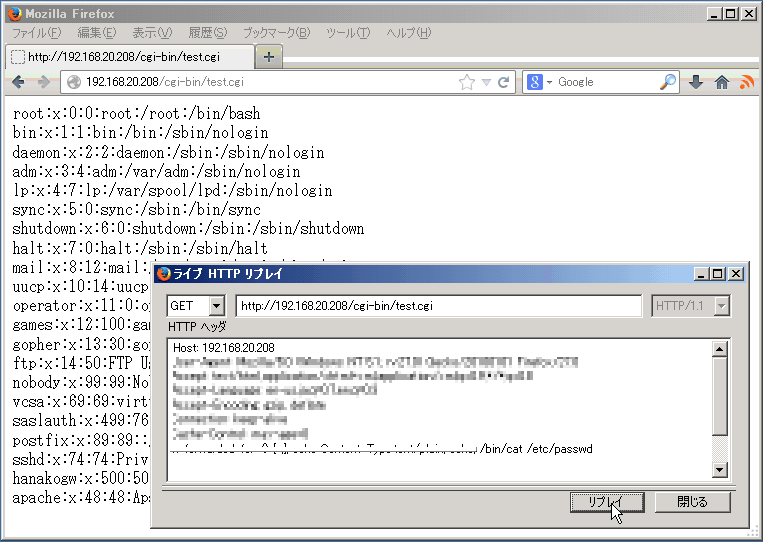
Figure 1. (Example) Arbitrary shell commands execution by specially crafted environment variables.
This issue is addressed in GNU Bash. Followings are security update of Linux distributions. Also, please refer to the advisories in "5. Product Information" of Hitachi.
+ AlaxalA Networks AX series <Products Confirmed Not Vulnerable>
[AX8600R/6700S/6600S/6300S, AX4600S/3800S/3600S/2400S]
[AX7800R/7700R/7800S/5400S]
[AX2500S/2200S/1200S]
[AX620R]
+ Hitachi Advanced Server HA8000 series <*>
+ Hitachi Advanced Server HA8500 series <*>
+ Client Blade FLORA bd100/bd500 series <*>
+ Thin Client FLORA Se210/Se330 series <*>
+ Hitachi bd Link <*>
+ Entry class disk array model BR1200 <*>
+ Tape Library L1/8A, Lx/24, Lx/30A, Lx/48, L20/300, L18/500, L56/3000, L64/8500 <*>
+ Hitachi UPS/Management software/Hitachi UPS option, PowerMonitor H, PowerMonitor H for Network,
SNMP interface card, Disk interface card, SNMP+Disk interface card <*>
+ Display/Keyboard unit/Switch Console Unit <*>
+ Hitachi Server Navigator Update Manager, Log Collect, Log Monitor, Alive Monitor, RAID Navigator <*>
+ Hitachi Server Navigator Installation Assistant <*>
<*>: <Products Confirmed Not Vulnerable>
+ Hitachi Metals Switch Apresia series <Products Confirmed Not Vulnerable>
+ Hitachi Metals XLGMC/XGMC/GMC/GMX/eWAVE/BMC/GMA series <Products Confirmed Not Vulnerable>
+ Hitachi Open Middleware Products <Products Confirmed Not Vulnerable>
+ Hitachi Storage Products
+ VFP(Hitachi Virtual File Platform)
+ Virtage(BladeSymphonyBS2000/BS500/BS320/BS1000 series)
Masato Terada (HIRT) and Naoko Ohnishi (HIRT)