Disaster Management and Security Solutions for a Safe and Secure Way of Life
Along with growing social instability in recent years, threats such as terrorism and crime having become more common and more diverse. This article describes work on area security that helps provide stronger security and more sophisticated business practices for social infrastructure by managing the movement of people and facilities on the basis of the visualization and analysis of information from the physical space obtained, using a platform developed by Hitachi, from sources such as physical security systems and Internet of Things sensors.

Security Business Planning Department, Security Business Strategy Division, Security Business Division, Service Platform Business Division Group, Services & Platforms Business Unit, Hitachi, Ltd. Current work and research: Planning of security businesses.

Business Management Department, Business Management Division, Security Business Division, Service Platform Business Division Group, Services & Platforms Business Unit, Hitachi, Ltd. Current work and research: Operation of privacy protection management systems.

Physical Security Solution Design Department, Physical Security Solution Division, Security & Image System Solution Group, Hitachi Industry & Control Solutions, Ltd. Current work and research: Integration of security solution businesses.

Solution Planning Department, Security Business Planning Division, Security & Image System Solution Group, Hitachi Industry & Control Solutions, Ltd. Current work and research: Planning of security businesses. Certifications: P.E.Jp (Professional Engineer, Japan) of Information Engineering and Certified Security System Expert.
The social infrastructure that supports people's way of life has found itself confronted by a variety of threats from terrorism and crime over recent years due to growing social instability and technological progress. Examples of such infrastructure include power plants, airports, railway stations, public places, factories, and theme parks.
Japan has a number of major international events coming up, while around the world instances of cyber terrorism with a significant impact on business continuity are taking place, as well as terrorist attacks in the form of bombings or shootings at places where people congregate. For reasons like this, strengthening security for social infrastructure is an urgent task.
With reference to the challenges facing security measures for social infrastructure, this article describes the potential for future developments in security using the Internet of Things (IoT), and also Hitachi's work on area security.
Various security guidelines have been produced by the government, industry, and individual operators on how to go about security measures for social infrastructure. When using these guidelines as a basis for implementing security measures, it is necessary for the infrastructure operator to decide on their core strategy, identify risks, and assess vulnerabilities, and then prioritize the measures to take. To achieve more robust security, it is particularly important to adopt a multi-layered defense-in-depth approach that combines actions on both the technical and operational aspects of cyber and physical security.
However, because of the view that security measures represent nothing more than a cost to social infrastructure operators, such that excessive measures impose a financial burden, decisions about these measures involve cautious evaluation. As a result, there are cases in which operators fail to decide on the appropriate scope of measures and put off security measures and enhancements despite existing vulnerabilities and outdated practices.
While security is essential to keeping social infrastructure safe and secure, Hitachi believes that the new value required for security solutions in the IoT era will be to help move operators' businesses forward through activities such as business improvement, overcoming management challenges, and new business creation, while expediting security measures and enhancements, and treating the expense of security measures not as a cost, but as an investment (see Figure 1).
Figure 1—Challenges Facing Security Measures for Social Infrastructure and Potential Future Developments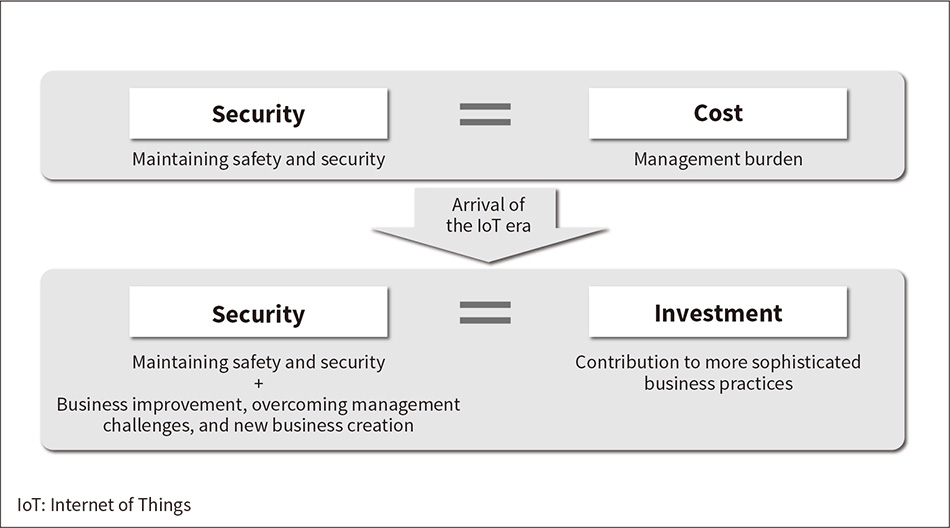 Ways of creating new value are needed that treat security measures as an investment rather than a mere cost for social infrastructure operators.
Ways of creating new value are needed that treat security measures as an investment rather than a mere cost for social infrastructure operators.
A key consideration when using security to help operators of social infrastructure to advance their businesses is the use of information and communication technology (ICT) to combine cyber and physical spaces, an idea put forth in the Society 5.0 concept being pursued by Japan's Cabinet Office.
Specifically, this involves the intensive collection of digital information about physical spaces by the physical security systems used to monitor people and facilities and the use of cyberspace to view and analyze their movements and circumstances, information that in the past could be acquired on only a fragmentary or sporadic basis. Hitachi believes that this will not only provide seamless surveillance of people and facilities, but also lead to the creation of new value, such as transforming this surveillance into information of value to the infrastructure operator or using it as feedback to physical spaces.
Hitachi has developed an integrated physical security platform to provide the foundations for this digital transformation.
The new integrated physical security platform works by using physical security systems (including security cameras and access control) and IoT sensors for acquiring locational information and environmental measurements to collect, store, and display information on physical social infrastructure (including operations and areas covered by surveillance). The platform also uses artificial intelligence (AI) or analytics software to analyze people and facilities (their movements, actions, and circumstances). In doing so, it provides a software platform for helping create value through initiatives such as strengthening security, making business improvements, overcoming management challenges, and developing new businesses (see Figure 2).
Figure 2—Overview of Integrated Physical Security Platform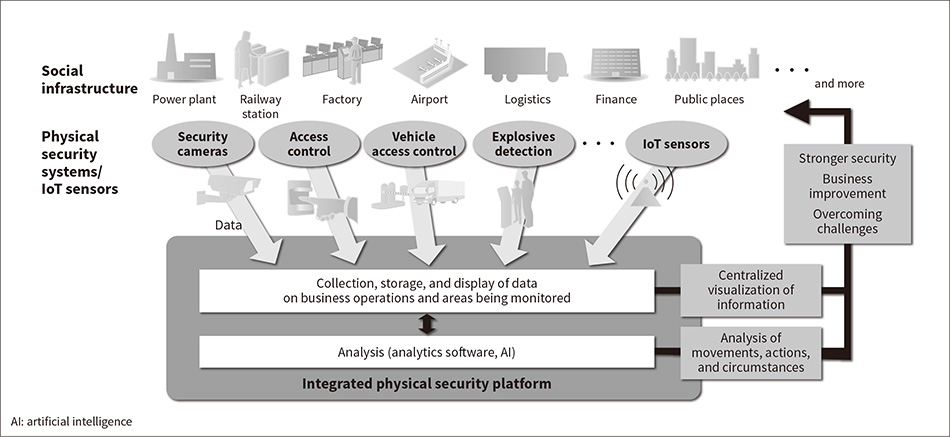 By collecting, storing, and displaying information about physical spaces, and analyzing the movement of people and facilities, the platform strengthens security and enables business improvement and the overcoming of management challenges.
By collecting, storing, and displaying information about physical spaces, and analyzing the movement of people and facilities, the platform strengthens security and enables business improvement and the overcoming of management challenges.
The platform software is broadly divided into three fields (see Figure 3).
While all three of these fields can run on-premises, it is also possible to configure the information and control and data fields in the cloud for convenience of administration and operation and have them interoperate with the physical field.
Hitachi offers a range of solutions according to the necessary security measures and customer requirements and issues by providing, in each field, a choice from the large number of standard plug-in modules that are available for the platform and that work with different systems, devices, and functions.
The physical field hosts modules that work with things like physical security systems, IoT sensors, and video analysis, while the information and control field has modules for the visualization, analysis, and control of the movement of people and facilities, covering report output and equipment control. The data field, meanwhile, along with handling data collection and storage, can also interoperate with the physical and information and control fields to manage activities on the administration side and provide feedback to the workplace.
Figure 3—Block Diagram of Integrated Physical Security Platform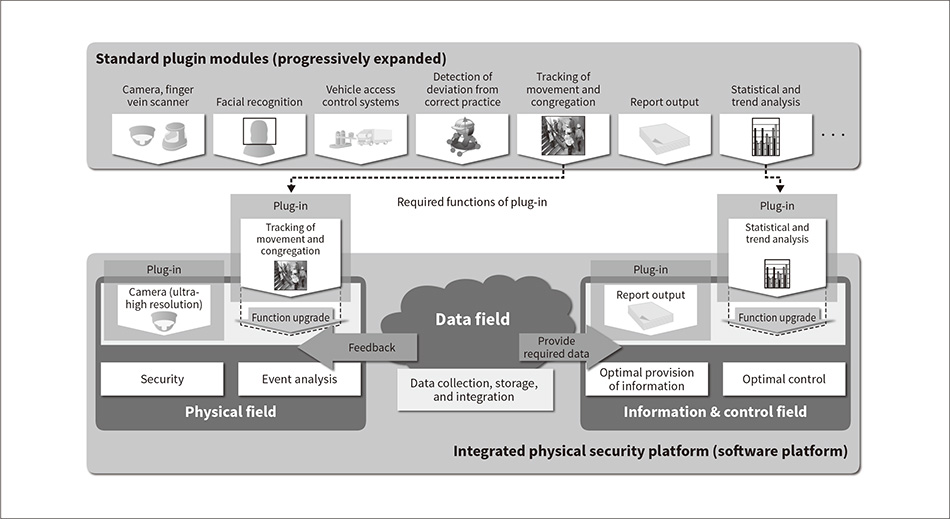 The platform works by plugging in the required functions for the physical field and information and control field, and by collecting, storing, and integrating data in the data field.
The platform works by plugging in the required functions for the physical field and information and control field, and by collecting, storing, and integrating data in the data field.
The structure and plug-in configuration describe above provide the platform with the following three major features.
Effective use can also be made of network resources when performing centralized management of a number of sites because functions can be split between on-premises and cloud hosts.
The platform can also be upgraded to the latest functions or integrated with existing systems and equipment by retrofitting analysis functions that use AI and business intelligence or modules that work with systems and equipment from other vendors.
Hitachi uses the term “area security” for security solutions that strengthen the security of social infrastructure or enable more sophisticated business practices.
The term can be used in relation to various forms of social infrastructure, including power plants, airports, railway stations, public places, factories, and theme parks. The following describes an example solution that uses the integrated physical security platform (see Figure 4).
Figure 4—Example Solution for Area Security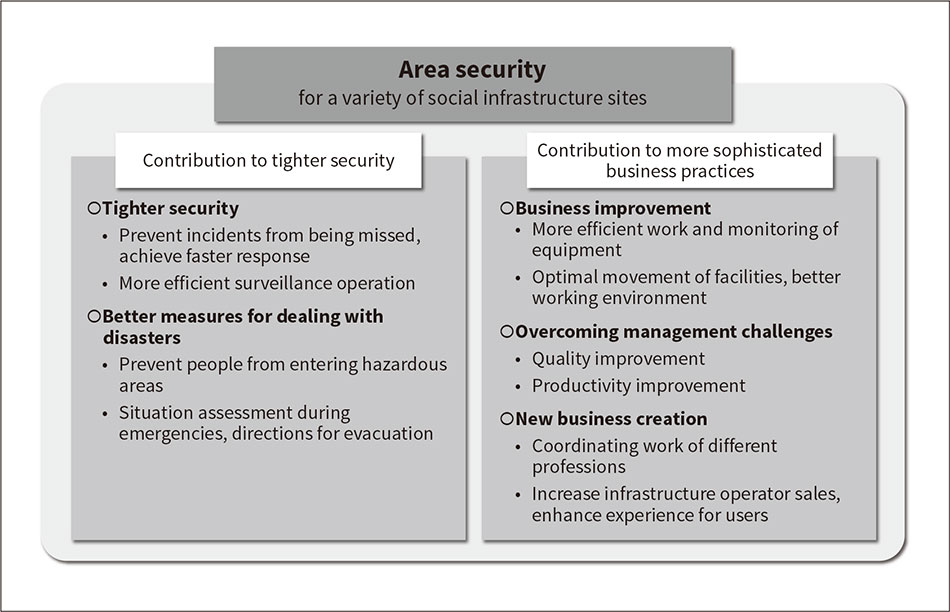 In addition to strengthening security, managing the behavior of people and facilities at a site can also help the business move forward by boosting operational efficiency and productivity.
In addition to strengthening security, managing the behavior of people and facilities at a site can also help the business move forward by boosting operational efficiency and productivity.
Among the consequences in the case of large systems that spanned multiple sites were higher costs for operating comprehensive surveillance and the failure to detect incidents (unauthorized people or items) due to incomplete surveillance.
In contrast, use of the platform enables the centralized collection and management of surveillance information through the integration of different physical security systems and IoT sensors, resulting in benefits that include more efficient operation through seamless surveillance and avoiding the misdetection of incidents. Similarly, the integration of video analysis functions can provide more robust surveillance and a rapid response by enabling automatic detection rather than relying on visual detection.
Because use of the integrated physical security platform enables seamless surveillance of staff, contractors, and others through the integration of different physical security systems and IoT sensors, work can be made more efficient by monitoring how different tasks are performed and detecting inefficient practices or irregular actions, and then providing feedback such as raising an alarm or issuing corrective instructions.
Similarly, efficiencies can also be achieved by monitoring what is happening with equipment, inventory, working environments, and other areas, and using this to automate monitoring for anomalies in equipment (work that would otherwise take a lot of time and people), formulate optimal plans for the movement of facilities based on accurate information on inventory levels, and improve conditions by detecting poor-quality working environments.
Use of the platform can boost quality and productivity by showing how tasks are actually being performed and using this information to identify and correct problems like contamination by foreign matter or unskilled practices, and to pass on skills to the younger generation by presenting the work of experienced staff as a model of good practices.
There is also scope for increasing the sales of infrastructure operators or providing a better experience for users by utilizing information from public places where users congregate for marketing purposes to encourage commercial activity, or by utilizing information about congestion or about individual users to provide the best possible services.
Careful attention needs to be paid to privacy when dealing with people's activities. Of particular note is the work done on identifying which matters businesses need to consider, with the IoT Acceleration Consortium (made up of participants from industry, government, and academia) having published a guidebook on the use of video footage and images.
With involvement in the use of data that goes beyond just video footage, Hitachi uses its own checklist to conduct privacy impact assessments, the content of which it is continually updating in line with the latest developments.
Through initiatives like these, Hitachi is taking preemptive steps to prevent privacy breaches from becoming a problem, being careful to handle personal data appropriately, including when supporting the operations of customer businesses.
This article has described Hitachi's work on area security.
It is important to understand the customer's situation and the challenges they face, and to work with them to choose the right solutions, plan their implementation, and consider operating practices.
In the future, Hitachi intends to advance the field of security and support stronger security and more sophisticated business practices for social infrastructure through measures such as the research and development of the latest technologies for creating value.