![]()
Last Update: June 12, 2017
AIS (Automated Indicator Sharing) is an information-sharing initiative involving a collaboration between private and public sectors, to share detected cyber attack indicators. Such indicators include the domains and IP addresses of servers controlling cyber attacks, and malware hash values. HIRT-PUB17007 introduces the information-sharing initiative AIS.
As shown in Figure 1, information can be utilized for cyber attack defensive measures, including both proactive and reactive measures. For proactive measures, information from collaborating organizations can be used to take defensive measures. For reactive measures, the information can be used to identify the damage caused by an attack. In some cases, the information can be utilized to perform high-level analysis: for example, identifying attributions of the threat actors and the attack activities.
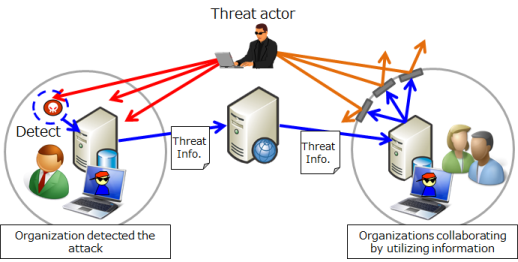
Figure 1: Using information from collaborating organizations to take proactive measures
In Japan, various organizations are striving to utilize information. These organizations include J-CSIP, ISACs (Information Sharing and Analysis Centers) including groups such as the ICT-ISAC Japan and Financials ISAC Japan, and the CSIRT (Computer Security Incident Response Team) community such as Nippon CSIRT Association.
For cyber attack defensive measures based on utilizing information, it is not enough to only have expert security specialists capable of collaboration via persons and performing high-level information analysis. It is also necessary to examine collaboration via systems to match the speed of a threat actor's activities and to respond immediately, even if such collaboration cannot perform high-level information analysis. (Table 1) When processing is done by a person, results might depend on that person's skill. Systematization where the results do not depend on skill levels is useful. Also, it is possible to alleviate the shortage of security specialists by systematizing and turning processes into routine work, which can then be performed even if expert security specialists are not present. For an information sharing initiative that supports the utilization of information, we need to consider both aspects (collaboration via persons and collaboration via systems).
Table 1: Information sharing initiative supporting the utilization of information
| For an earthquake | For defensive measures against cyber attacks | |
| Collaboration via systems (computer-based information sharing, machine-readable) | Fast reports on earthquakes, delivered by email | Systematization that uses STIX and TAXII etc. (Example: AIS) |
| Collaboration via persons (human-based information sharing, human-readable) | News conferences by the Meteorological Agency | Collaboration using email, SNS, etc. |
AIS is a result of the CISA (Cybersecurity Information Sharing Act). AIS activities started under the DHS (Department of Homeland Security) from March 2016. In AIS, cyber attack indicators are collected. Such indicators include threat information such as the domains and IP addresses of servers controlling cyber attacks, and malware hash values. The collected cyber threat information is analyzed at the NCCIC (National Cybersecurity and Communications Integration Center) and the indicators, in which the cyber threat information is discribed, are distributed. Table 2 and Figure 2 show the procedures for receiving indicators from AIS and for submitting indicators to AIS.
Table 2: Receive and submit indicators from/to AIS
| Input/Output | Procedure | Application submitted in advance |
| Receiving indicators from AIS | (a) Receiving indicators by using STIX and TAXII | Required |
| Submitting indicators to AIS | (b) Submitting indicators by using STIX and TAXII | |
| (c) Submitting indicators by using a web form | Not required | |
| (d) Submitting indicators by using email |
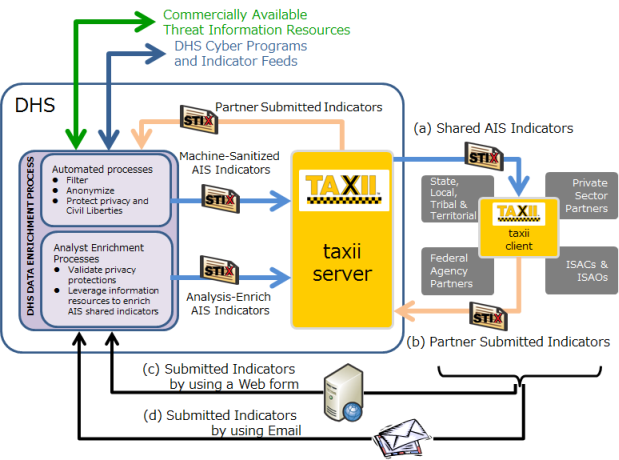
Figure 2: AIS
An indicator indicates a cyber attack characteristic that is useful for detecting and identifying an attack. For example, as shown in Figure 3, reception of an email with a malware attachment (invitation.zip and meeting20170401.exe) results in access to the malicious site Mal.CyberAttack.com. In this case, items such as those in Table 3 become the indicators. By providing items common to cyber attack activities as indicators, the utilization of information becomes more effective.
Table 3: Example of indicators
| Category | Item | Example | |
| From | attacker@CyberAttack.com | ||
| Subject | Cybersecurity Workshop 2017 at AK building | ||
| Attached files | File name | invitation.zip | meeting20170401.exe |
| Hash value | 1d11060375445e4627bfef57c28af44b | 69ab49f89461bf1e4d696e2d21e36dcf | |
| URL | Mal.CyberAttack.com | ||
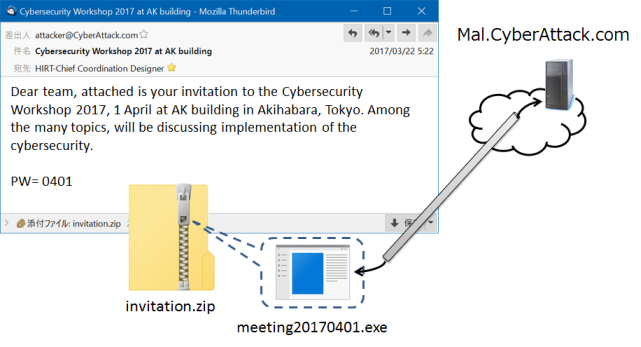
Figure 3: Receiving a suspicious email with attached malware that accesses a malicious site
- Specifications for describing cyber attack activities -
To take a bird's eye view of cyber attack activities, we need to summarize the status related to the threat actor and the status related to the defending side. Information related to the threat actor includes the threat actor (the persons or organizations participating in a cyber attack), the threat actor's activities and methods, and the targeted system vulnerabilities, etc. Information related to the defending side includes the signs that enable the cyber attack to be detected, and the defensive measures that should be taken against the cyber attack, etc. STIX provides a structured method for describing threat information. It was developed to enable the descriptions of such related information to be written in a standardized way. In addition, STIX was developed to enable the analysis of cyber threats and cyber attacks, to identify characteristics associated with cyber attacks, to manage cyber attack activities, and to share information related to cyber attacks. An indicator is one collection of information in which threat information is written. An indicator describes the characteristics of a cyber attack that are useful for detecting an attack, from among the various events observed in a cyber attack.
- Specifications for exchanging information about cyber attack activities -
To exchange information about cyber attack activities, various items must be decided for the procedure for exchanging information: for example, the service definitions, the procedure for transfers used by the service, and the method specifications, etc. TAXII is a procedure for the automated exchange of indicator information. TAXII was developed to exchange threat information related to cyber attack activities. Such information is written in STIX, which provides a structured method of describing threat information (Figure 4).
The STIX and TAXII specifications developed from 2012, mainly by DHS and MITRE. However, management of the specifications was transferred to OASIS in July 2015. In May 2016, the following editions were released: the OASIS edition of STIX Ver. 1.2.1 (which had the same specifications as the MITRE edition of STIX Ver. 1.2), and the OASIS edition of TAXII Ver. 1.1.1 (which had the same specifications as the DHS edition of TAXII Ver. 1.1). The following versions of the specifications are being developed.
HIRT is striving to spread the information sharing initiative, as one link in the defensive measures against cyber attacks. On May 3, 2017, HIRT completed their connection to the AIS system (to the TAXII server). The subsections below describe the path followed to establish a connection to the AIS system, in order to receive indicators from AIS and to submit indicators to AIS.
Table 4 shows the general application procedure until the connection to the AIS system was established.
Table 4: Application procedure
| # | Application procedure | Events |
| 1 | Submit the AIS Terms of Use | October 24, 2016: Signed and submitted the AIS Terms of Use. |
| 2 | Prepare the TAXII client | Middle of November 2016: Prepared a custom TAXII client for connecting to the AIS system. |
| 3 | Obtain a PKI certificate. Notify DHS of the IP address, and submit the Interconnection Security Agreement. | October 27, 2016: Signed and submitted the Interconnection Security Agreement, which completed the steps for affiliation. It is necessary to obtain a PKI certificate that is equivalent to a U.S. government issued PKI certificate. Therefore, we did the following: (i) On March 8, 2017, we obtained our PKI certificate from a Japanese domestic PKI certificate vendor, and (ii) On February 23, 2017, we obtained the equivalent directly from a U.S. PKI certificate vendor. In particular, as the forerunner, we believed we should establish a method that would enable a PKI certificate to be obtained even in Japan. April 11, 2017: Notified DHS of the IP address that would be used to access AIS. |
| 4 | Connect to the AIS system (to the TAXII server) | May 3, 2017: Received a "Welcome to AIS" email from the DHS, which completed our preparation for connecting to the AIS system. On the same day, we confirmed that the custom TAXII client could receive indicators. |
The key point in the application procedure is obtaining the PKI certificates used to connect to the AIS system. The PKI framework of the U.S. government is of a form that uses two PKI certificates.
This is a PKI certificate that follows the naming conventions of the U.S. Federal PKI Common Policy Framework, which controls and regulates U.S. government PKI components. The PKI certificate we obtained directly from the U.S. PKI certificate vendor is of this form (We obtained a PKI certificate from Operational Research Consultants, which is the PKI certificate vendor recommended by AIS.).
This is a PKI certificate participating in those issued by FBCA (The Federal Bridge Certification Authority). The FBCA is a certification authority for the mutual operation of PKIs. Figure 5 shows the mutual cross-certification of the FBCA and private sector certification authorities. This mutual certification enables the PKI certificates issued by private sector certification authorities to be treated as equivalent to the PKI certificates issued by the U.S. government. The PKI certificate obtained via a PKI certificate vendor within Japan is of this form (We obtained a PKI certificate issued by DigiCert via Cybertrust Japan.).
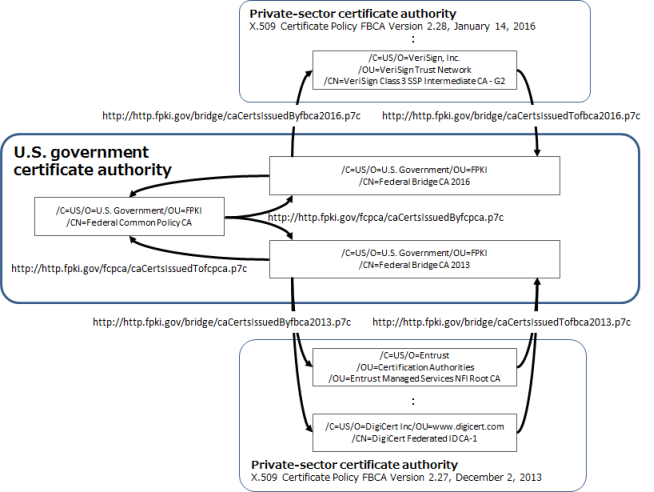
Figure 5: Mutual Cross-Certification of the FBCA and private-sector certification authorities
Masato Terada (HIRT), Naoko Asai (HIRT) and Naoko Ohnishi (HIRT)