January 9, 2024
Hitachi has developed a model that can efficiently estimate and assess the vulnerability of software products using AI, based on publicly available information on vulnerabilities, even when detailed information on the configuration of software is not available from suppliers.
Some outputs of this work has been published in the December 2023 issue of the Journal of Information Processing Society of Japan.
In conventional vulnerability assessment, incident response teams (PSIRTs)*1 manually analyze vulnerability reports, patch notes, and security advisories released by software vendors and security agencies, to determine whether their software products contain problematic components. Hitachi proposes a new two-step vulnerability assessment model as shown in Figure 1. In the step 1, the customer's PSIRT automatically extracts vulnerabilities estimated to be associated with the product from a knowledge graph*2 database (DB) using AI, and in the step 2, the PSIRT identifies vulnerabilities using information obtained in the step 1.
To validate this model, we created a knowledge graph DB from publicly available vulnerability data and developed a function to automatically extract information on vulnerabilities estimated to be associated using AI. In the future, we will develop a function to collect vulnerability information from websites and build a knowledge graph DB using natural language processing technology while understanding the needs of customers in various fields, to contribute to the enhancement of software supply chain security*3.
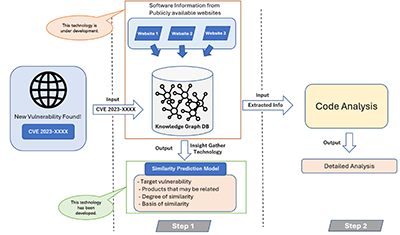
Fig. 1. Block diagram of two-step vulnerability assessment
For more information, use the enquiry form below to contact the Research & Development Group, Hitachi, Ltd. Please make sure to include the title of the article.