![]()
(VU#720951, CVE-2014-0160)
Last Updated: May 12, 2014
OpenSSL 1.0.1 contains a vulnerability that could disclose sensitive private information to an attacker. This vulnerability is commonly referred to as "heartbleed."
Base Metrics: 5.0
Access Vector: Network
Access Complexity: Low
Authentication: None
Confidentiality Impact: Partial
Integrity Impact: None
Availability Impact: None
Temporal Metrics 4.1 (April 16, 2014)
Exploitablity: Functional exploit exists
Remediation Level: Official fix
Report Confidence: Confirmed
+ OpenSSL 1.0.1 to 1.0.1f
+ OpenSSL 1.0.2-beta to 1.0.2-beta1
+ Hitachi Products that use OpenSSL
By attacking a service that uses a vulnerable version of OpenSSL, a remote, unauthenticated attacker may be able to retrieve sensitive information, such as secret keys or session IDs.
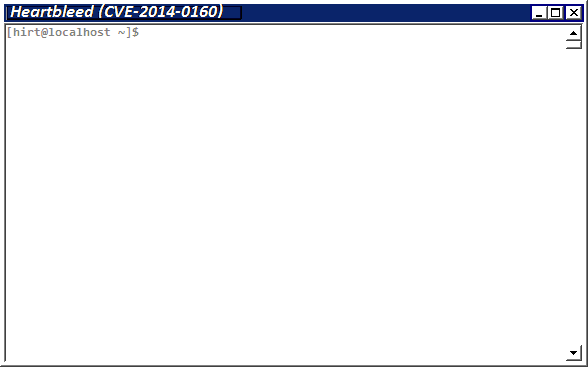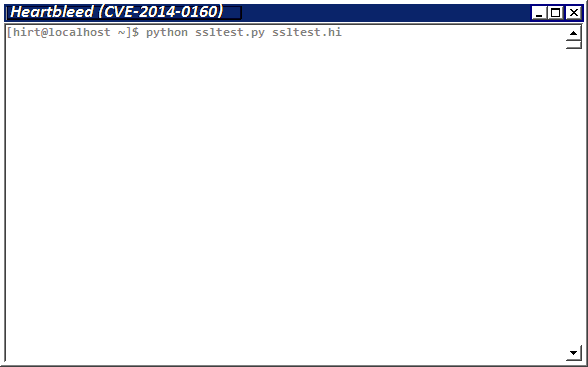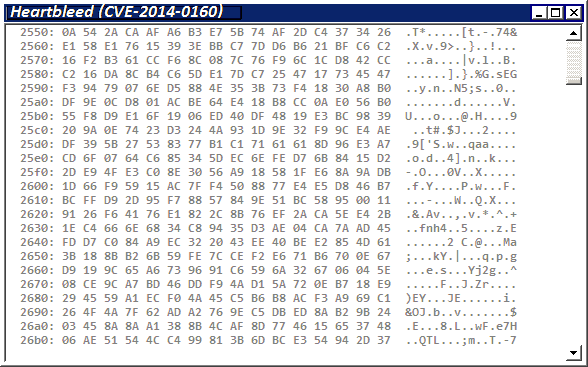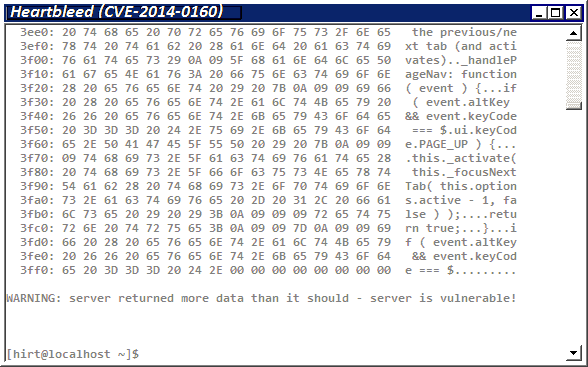
Figure 1. (Example) Information leak of the data stored in the memory of SSL server.
This issue is addressed in OpenSSL 1.0.1g. Please refer to the advisories of each product.
Any system that may have exposed this vulnerability should regenerate any sensitive information (secret keys, passwords, etc.) with the assumption that an attacker has already used this vulnerability to obtain those items.
#1: New Keys: For all affected systems, acquire new key certificates, revoke your old ones and install the new ones.
#2: Change Passwords: Once you have patched your systems, changed your keys, ensure that your systems also accomplished those tasks, then it is time to change the passwords for all users on those systems. Do not do this until everything else is done.
+ Control Server & Controller: RS90 series, S10 series, HISEC series <Products Confirmed Not Vulnerable>
+ Industrial Computer: HF-W series <Products Confirmed Not Vulnerable>
+ Industrial Control Platform: HIACS-AZ series, PS21 series <Products Confirmed Not Vulnerable>
+ DCS Platform: HIACS series <Products Confirmed Not Vulnerable>
+ Hitachi Metals XLGMC/XGMC/GMC/GMX/eWAVE/BMC/GMA series <Products Confirmed Not Vulnerable>
+ Hitachi IT Operations <Products Confirmed Not Vulnerable>
+ Virtage <Products Confirmed Not Vulnerable>
+ Virtage Navigator <Products Confirmed Not Vulnerable>
+ HVM Administration Command (HvmSh) <Products Confirmed Not Vulnerable>
+ Hitachi Advanced Server HA8000 series
+ BladeSymphony BS2000 series
+ BladeSymphony BS500 series
+ JP1/VERITAS Backup Exec <Products Confirmed Not Vulnerable>
+ JP1/Hibun <Products Confirmed Not Vulnerable>
+ Hibun AE Full Disk Encryption <Products Confirmed Not Vulnerable>
+ JP1/VERITAS NetBackup
+ ALC NetAcademy2 <Products Confirmed Not Vulnerable>
+ Router / Switch GS/GR series <Products Confirmed Not Vulnerable>
[GS3000/GS4000]
[GR2000/GR4000]
+ Hitachi Metals Switch Apresia series <Products Confirmed Not Vulnerable>
+ (VSP) Hitachi Virtual Storage Platform
+ (HUS VM) Hitachi Unified Storage VM
+ AlaxalA Networks AX series <Products Confirmed Not Vulnerable>
[AX8600R/6700S/6600S/6300S, AX4600S/3800S/3600S/2400S]
[AX7800R/7700R/7800S/5400S]
[AX2500S/2200S/1200S]
[AX620R]
+ Hitachi Open Middleware products <Products Confirmed Not Vulnerable>
+ Hitachi Command Suite (Storage and Server Administration) <Products Confirmed Not Vulnerable>
Masato Terada (HIRT) and Naoko Ohnishi (HIRT)