![]()
Last Update: April 17, 2017
Jakarta Multipart parser of Apache Struts 2 mishandles file upload, that may allow an attacker to remotely execute arbitrary code via crafted HTTP requests.
This vulnerability affecting the Apache Struts 2 has been exploited in the wild. Users and administrators are encouraged to review the Apache Security Bulletin and upgrade to fixed version.
March 06, 2017
The Apache Software Foundation released security bulletin (S2-045). Proof of Concept code has released.
March 07, 2017
Functional exploit code has released.
March 07, 2017 10:12 CST
Arbitrary code execution based exploit code has released.
March 07, 2017 06:21 UTC
Metasploit-framework has released CVE-2017-5638 module.
March 07, 2017 15:36 UTC
Some arbitrary code execution based exploit codes have released.
March 08, 2017
The Apache Software Foundation released Struts 2.3.32 and Struts 2.5.10.1.
March 21, 2017
The Apache Software Foundation released security bulletin (S2-046). Content-Dispostion / Content-Length value is a different vector for the same vulnerability in S2-045 (CVE-2017-5638).
CVE-2017-5638: Possible Remote Code Execution when performing file upload based on Jakarta Multipart parser.
CVSSv2 Base Score
CVSS:2.0/AV:N/AC:L/Au:N/C:C/I:C/A:C/E:H/RL:OF/RC:C
AV: Attack Vector= Network
AC: Access Complexity= Low
Au: Authentication= None
C: Confidentiality= Complete
I: Integrity= Complete
A: Availability= Complete
CVSSv3 Base Score
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:H/RL:O/RC:C
AV: Attack Vector= Network
AC: Attack Complexity= Low
PR: Privileges ReqPRred= None
UI: User Interaction= None
S: Scope= Changed
C: Confidentiality= High
I: Integrity= High
A: Availability= High
Temporal Socre (as of March 16, 2017)
E: Exploit Code Maturity= High
RL: Remediation Level= Official Fix
RC: Report Confidence= Confirmed
+ cpe:/a:apache:struts:2.3.5 - cpe:/a:apache:struts:2.3.31
+ cpe:/a:apache:struts:2.5 - cpe:/a:apache:struts:2.5.10
This vulnerability allows remote attacker to execute arbitrary code via crafted HTTP requests.
Users and administrators are encouraged to upgrade to fixed version.
(Fix) Upgrade to fixed version.
March 08, 2017, The Apache Software Foundation released Struts 2.3.32 and Struts 2.5.10.1.
(Workaround) Implement a Servlet filter
Implement a Servlet filter which will validate Content-Type / Content-Dispostion / Content-Length and throw away request with suspicious values not matching multipart/form-data.
[Notice]
JakartaStreamMultiPartRequest is vulnerable to variant exploit approach of "Content-type: malicious". Upgrade to Apache Struts version 2.3.32 or 2.5.10.1 is recommended. S02-045 Solution "You can also switch to a different implementation of the Multipart parser." is not recommended.
March 15, 2017: Confirmed "JakartaStreamMultiPartRequest is vulnerable".
March 16, 2017: Reported to JPCERT/CC.
March 17, 2017: Confirmed JPCERT-AT-2017-0009 revised version and disclosed HIRT-PUB17006.
March 21, 2017: Confirmed "S2-046 is same issue".
Security Advisory HIRT-PUB17006 was released.
+ HiRDB Control Manager - Server
hitachi-sec-2017-110: Vulnerability in HiRDB Control Manager - Server
This vulnerability has been assigned the following enumeration.
JakartaStreamMultiPartRequest is vulnerable to variant exploit approach.
Verification environment is the followings.
+ Ubuntu 16.04.1 (Linux 4.4.0-66-generic)
+ Tomcat 8.0.32
+ Struts 2.3.30
Proof of Concept code send crafted HTTP request with addHeader('X-Check-Struts', 'S2-045 VULNERABLE!!'). Also HTTP response includes it as the header.
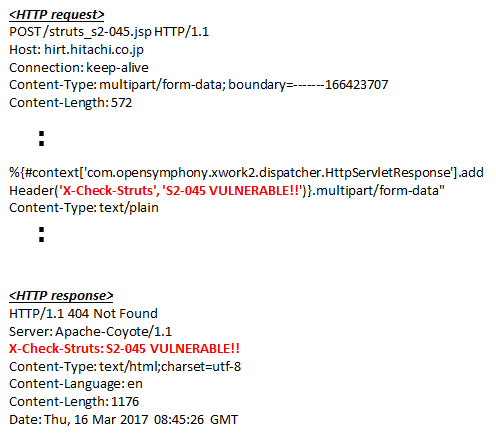
Fig2: Verification of variant exploit approach under JakartaStreamMultiPartRequest.
Masato Terada (HIRT) and Naoko Ohnishi (HIRT)