Unauthorized communication data can be judged and eliminated in about two microseconds
September 19, 2019
Hitachi, Ltd. today announced newly developed technique for firewalls which can be applied to high-speed control systems used in fields such as power transmission and distribution systems and factory automation. This technique includes a unique logic circuit which implements a judgment algorithm in "software-less" manner and data invalidation method, which can judge and eliminate unauthorized communication data in about two microseconds. Enhancing security for control devices such as DCSs*1 and PLCs*2 operating with a control cycle time of 10 milliseconds or less, as well as monitoring terminals and control servers, has been difficult with existing firewalls designed for IT networks; however, the developed technique makes it possible regardless of device type or whether the installation is new or existing [see Figure 1]. It is thus expected to reduce loss costs such as damage to plant equipment caused by cyber attacks. From now onwards, Hitachi will practically verify these developed technology so that it contribute to improving the security of control systems.
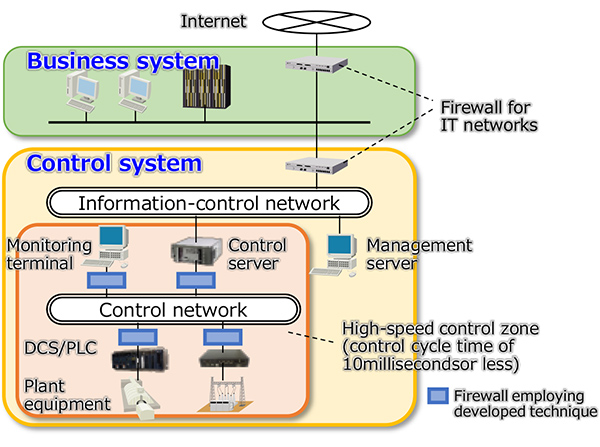
Figure 1: Examples of security measures using the developed technique
The following architecture and method have been developed for reducing the judgement time.
The result of implemention and evaluatiion of this technique on a FPGA*3 confirmed that the communication data can be judged in 2.12 to 2.2 microseconds through the firewall, which is sufficiently shorter than the control cycle time of general factory automation (1 to 10 milliseconds).
Firewalls judge if incoming communication data is authorized or not by checking it with predefined rules. In conventional firewalls, the entire packet of communication data is stored in memory and then checked with the rules by software processing [see Figure 2(a)]; consequently, it sometimes stays in the firewall for a long time, depending on conditions such as data length and incoming frequency. To avoid such situation, new firewall architecture [see Figure 2(b)] has been developed. It employs a unique logic circuit implementing an algorithm to check incoming communication data without software processing using a CPU or memory. The communication data is checked with rules sequentially as it flows through the circuit, so it stays in the firewall only for significantly short time.
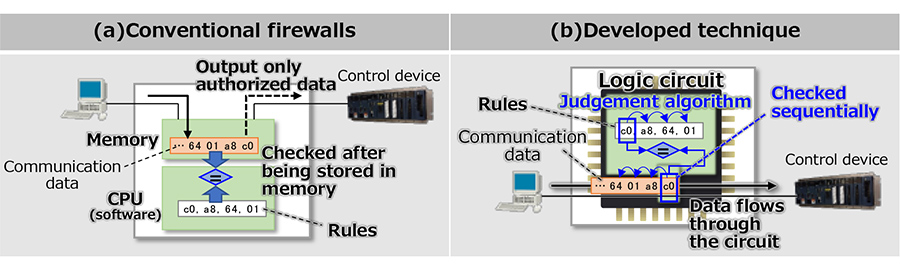
Figure 2: Judgment of unauthorized communication data (comparison with conventional)
In conventional firewalls, communication data will be sent out after being checked entirely and judged if it is authorized or not, which also cause the data to stay for a long time in the firewall. In the developed method, the communication data is sent out before checking is completed and thus regardless of if it is authorized or not. Instead, when the communication data has been judged as unauthorized, its FCS*4 field located at the tail is modified [see Figure 3]. Communication data with modified FCS is judged to be corrupted and will not be received at its destination device; thus the attempt of cyber-attack will not succeed. Since the firewall can invalidate unauthorized communication data after sending it out, it can begin sending the data before completeing checking and judging, which contributes to further shortening staying time.
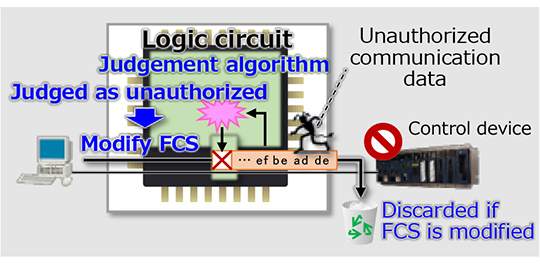
Figure 3: Invalidation of invalid communication data
For more information, use the enquiry form below to contact the Research & Development Group, Hitachi, Ltd. Please make sure to include the title of the article.