The Solution to Vulnerability Issues Left in Operational Technology Systems, Where Unexpected Downtime is not Permitted
February 9, 2023
Hitachi, Ltd. has developed Security Digital Twin (SDT) technology that facilitates the planning of security countermeasures ensuring business continuity*1. Capitalizing on the security expertise amassed by Hitachi in operational technology (OT) systems*2, this technology reproduces digital twins in cyber space comprising actor, asset, and process models to simulate OT systems in physical space. Customers can identify high-risk vulnerabilities and propose multiple effective security countermeasures to evaluate the impact each has on business continuity (side effects) before implementing any of those security countermeasures in an OT system. Customers can then properly plan security countermeasures based on the assessment results of these side effects so that they can align with their key performance indicators (KPI).
Hitachi will use this technology in the future to help optimize and drive the efficiency of security countermeasures for IoT devices as well as connected cars, medical equipment systems and other social infrastructure, such as power plants.
Hitachi announced some aspects of security digital twins at The SICE Annual Conference 2022 on September 7, 2022. This technology also received the Achievement Prize for Industrial Applications from the 2022 Society of Instrument and Control Engineers (SICE) Annual Conference Award on November 15, 2022.
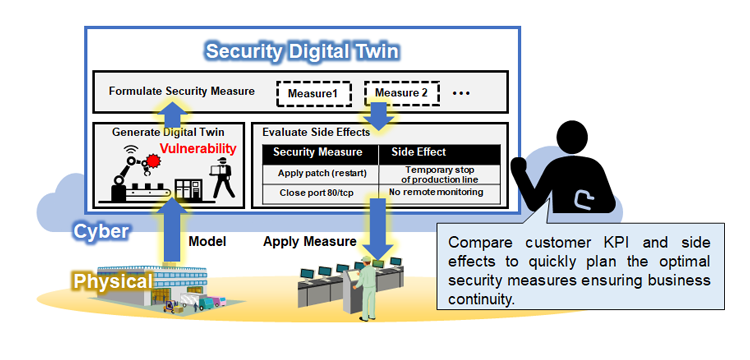
Fig. 1. Conceptual diagram of the security digital twin technology
In recent years, cyber attacks against OT systems are rapidly increasing, and there is an urgent need for the improvement of cyber security in OT systems as well as IT systems. However, vulnerabilities of OT systems are often left unmitigated for a long time compared to IT system as security countermeasures, such as patching and changing firewall rules, could result in unexpected downtime.
Hitachi develops the SDT to solve the issue. The SDT can plan security countermeasures that can reduce the risk of cyber attacks, and also evaluate side effects caused by each security countermeasure, such as system halt. The technological features of the SDT are outlined below.
(1) Technology to build digital twins of OT systems with three-layer models
OT systems in physical space are reproduced by three-layer models consisting of the actor, asset and process models in cyber space to evaluate side effects on business continuity (Fig. 2). The actor model reproduces the behavior of operators who are involved in daily operations, attackers who make negative impacts on the system, and defenders who implement security countermeasures. The asset model represents the information of computers in OT systems, including software vulnerabilities and network dependencies. The process model reproduces how critical business processes are conducted. By dividing the digital twin into three layers, experts in each field can quickly and accurately construct models independently, and then integrate them using common interfaces. Finally, a state transition program that links three-layer models is used to reproduce the behavior of each model in time series.
An example of how the program works is as follows: Users can activate an attacker model to attack the asset model and then identify high-risk vulnerabilities. Next, users activate a defender model to apply multiple plans of security countermeasures that mitigate the risk of cyber attacks, and finally evaluate side effects, i.e., the level of degradation in the business performance, of each plan.
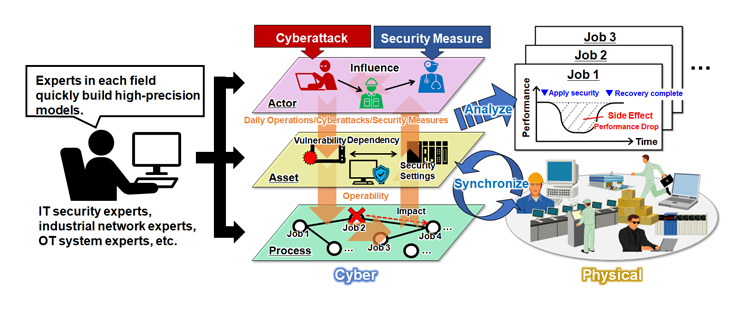
Fig. 2. Technology to configure digital twins of OT systems using three-layer models
(2) Productivity calculation models for IoT environments at factories
To apply this technology in a factory environment, Hitachi set forth “maintaining the production rate of lines” as a KPI and developed a model calculating the impact of security countermeasures on productivity. Fig. 3 shows a digital twin of the production process built using Petri nets*3. The model shows the state of products represented in cyber space by tokens (black circle) after a number of manufacturing steps, and calculates the production rate from the number of tokens that have completed all manufacturing steps. Moreover, such technology to automatically generate production models from operational logs accumulated by the production management system enables customers to quickly build the SDT for different factory environments.
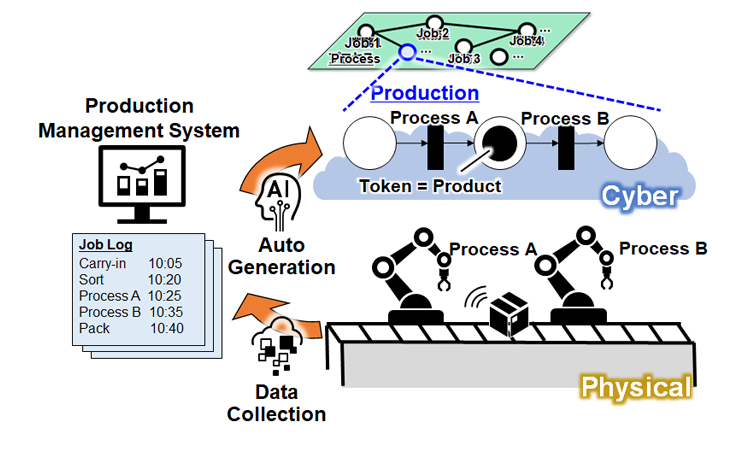
Fig. 3. Model to calculate the impact of security countermeasures on production rate in a factory environment
The use of Petri nets also enables modeling of other business operations, for example production, quality assurance, or remote monitoring, as shown in Fig. 4. If the SDT identifies high-risk vulnerabilities and multiple security countermeasure patterns, optimal mitigations can be planned based on the customer’s KPI and side effects for each countermeasure. The example shown in Fig. 4 illustrates a customer prioritizing production and quality assurance processes as KPIs, while tolerating outage of remote monitoring services. Selection of security countermeasure no. 2 most closely matches the customer’s requirements, enabling a rapid deployment in the OT system.
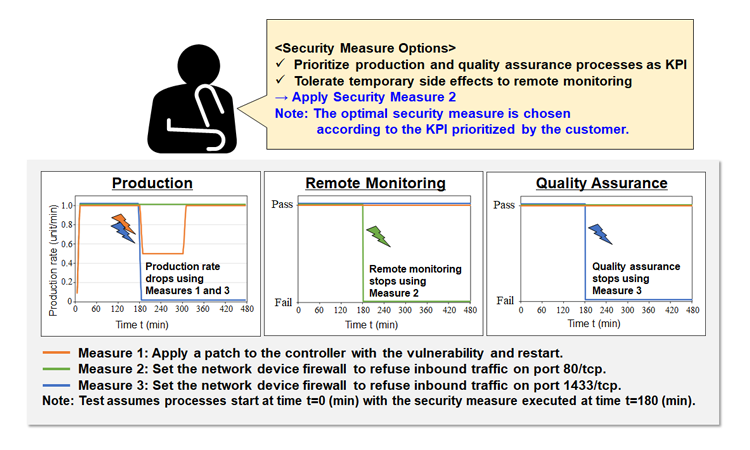
Fig. 4. Example of security options taking into account side effects
For more information, use the enquiry form below to contact the Research & Development Group, Hitachi, Ltd. Please make sure to include the title of the article.