In a society advancing remote access and digital technologies, biometric authentication has become essential as the easiest and most reliable authentication technology to verify the identities of users. However, the challenge is to achieve both user friendliness as well as secure management of private data, including biometric information. Hitachi, Ltd. (hereinafter “Hitachi”) developed Public Biometric Infrastructure as a solution to overcome these challenges. We sat down to talk with Principal Researcher Kenta Takahashi from the Research and Development Group about the actual system and its usage.
(March 25, 2022)The world has dramatically changed with a shift to a new normal brought by the COVID-19 pandemic and the promotion of a digital transformation (DX). One main driving force of these changes is the advancement of remote access technologies. This is not limited to services in the IT industry. Whether finance, retail, education, healthcare, or government, a wide range of sectors throughout society are expanding remote services. A very important aspect of these remote services is establishing trust in cyberspace, which also increases the necessity of authentication technologies to support the establishment of trust.
This means that we had better define what exactly is authentication in cyberspace. Authentication is the use of a digital identity—data attributes about a person—to validate a person as a specific user (individual). The biggest task to verify whether users are who they say they are is supporting the trust built between people in society. We do not ask for a verbal password or identification card when a spouse comes home to make sure they are who they say they are. Human beings use a vast amount of living physical information to identify others from visual and optical perception to auditory, tactile, and other sensory information.
The digital world is a non-face-to-face environment though, which makes identifying one another difficult. I could contact you and say, “It’s Takahashi. Could you wire me a million yen?” In the digital world however, there is no way for you to distinguish whether or not it is really me (Takahashi). The real world has an overwhelming variety and volume of information compared to the digital world where not enough amount of information can be obtained to accurately identify anyone. The other problem is the ability to infinitely copy digital information. Unique identifiers, or authentication information, are indispensable in identifying a person in such a digital world.
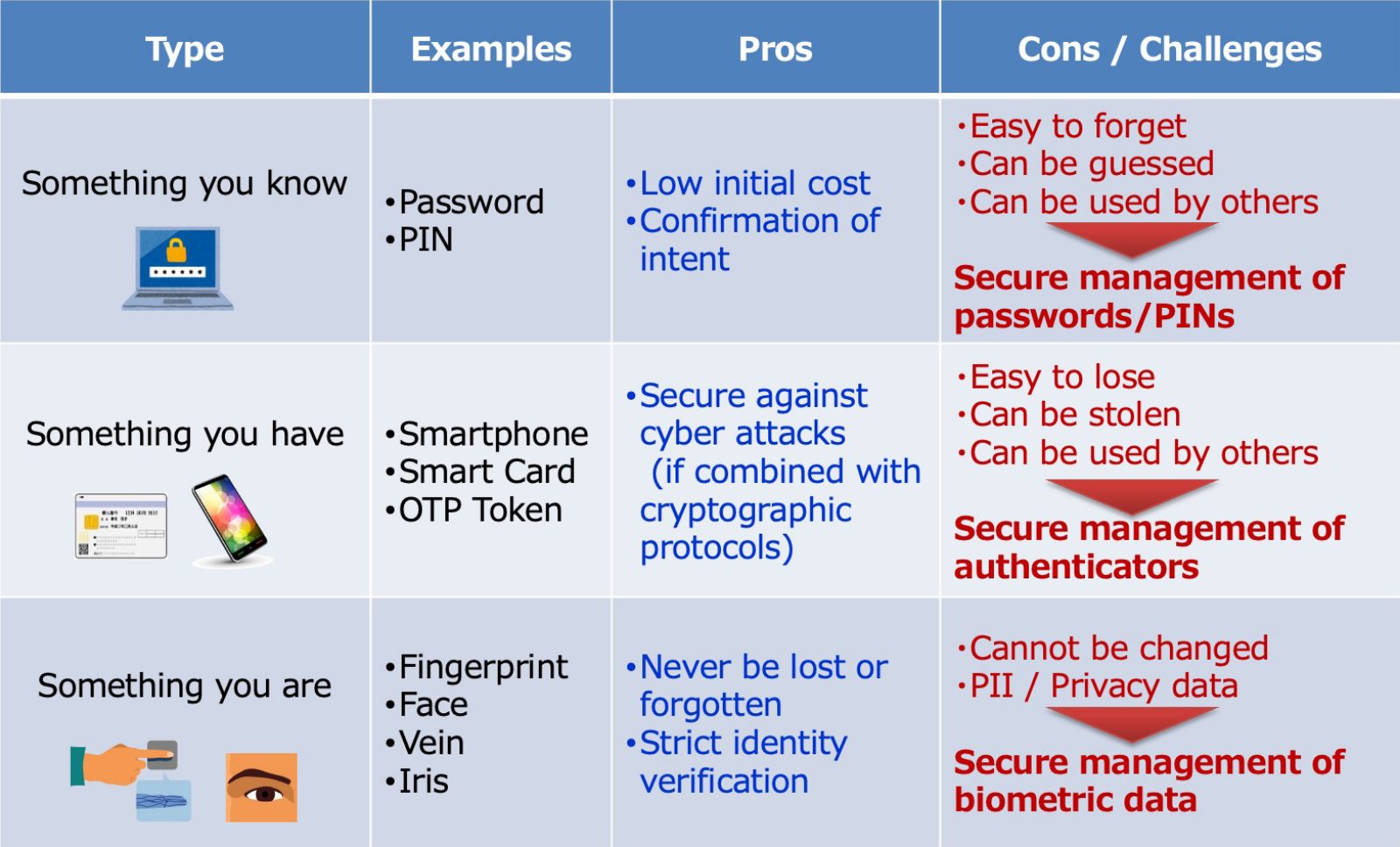
Let us take a moment now to review a few basic types of authentication information. The three factors of authentication are: something you know, something you have, and something you are. Something you know is authentication using secret information you remember, such as a password or personal identification number. Something you have is authentication using your possession like a smartphone or a smart card storing credential information such as an authentication key. Something you are is biometric authentication, such as a fingerprint, a face, or even vein patterns. Of these three authentication factors, something you know has become more compromised than ever with frequent large data leaks of passwords and unauthorized access. Something you have comes with the problems of theft and illicit transfer as well as issues of convenience, such as losing or forgetting something used for authentication. Conversely, there are growing expectations for biometric authentication and its use is expanding as a secure and highly user-friendly means of authentication that uses the physical features and characteristics of a person.
Another standpoint is the secure management of private authentication information, which has been a common and fundamental problem of authentication. Secure management is required not only for passwords but also for biometric data in the case of biometric authentication. Public Key Infrastructure (PKI) based on secure cryptographic technologies is no exception and has suffered from the “key management problem.” Any breach of private authentication information compromises the security of a system. In particular, the compromise of biometric data comes with serious social and economic risks because users cannot simply reset this personal data. In this way, secret management is a central issue and can be seen as the Achilles’ heel of authentication.
Authentication methods to transfer biometric data or passwords to servers through the Internet increase the risk of privacy and security . That is why the Fast IDentity Online (FIDO) Alliance created the FIDO Authentication standard. Typically, FIDO protocols execute biometric verification within user’s computers, smartphones, or another client devices where the user’s biometric data and cryptographic private keys are stored. Once biometric verification has succeeded, the cryptographically secure authentication protocol between the client device and the server is executed based on the private key and corresponding public key, without sending or receiving biometric data over the Internet. These protocols have become a de facto standard because there is no danger of leaking passwords and lower privacy risks to biometric data. FIDO protocols are even expanding for online banking and other such applications on smartphones.
To use FIDO protocols however, devices must keep and securely manage both the biometric data and a private key as confidential authentication data which must never be leaked. Therefore, this authentication standard only allows users to access services from devices where their biometric data and private key have been registered. This limitation makes it difficult to use FIDO protocols for devices shared by a large number of unspecified users, such as store payment devices, bank ATMs, and entrance gates of buildings and other facilities. Another issue is the loss of access to services if a user loses or changes his/her smartphones or PCs.
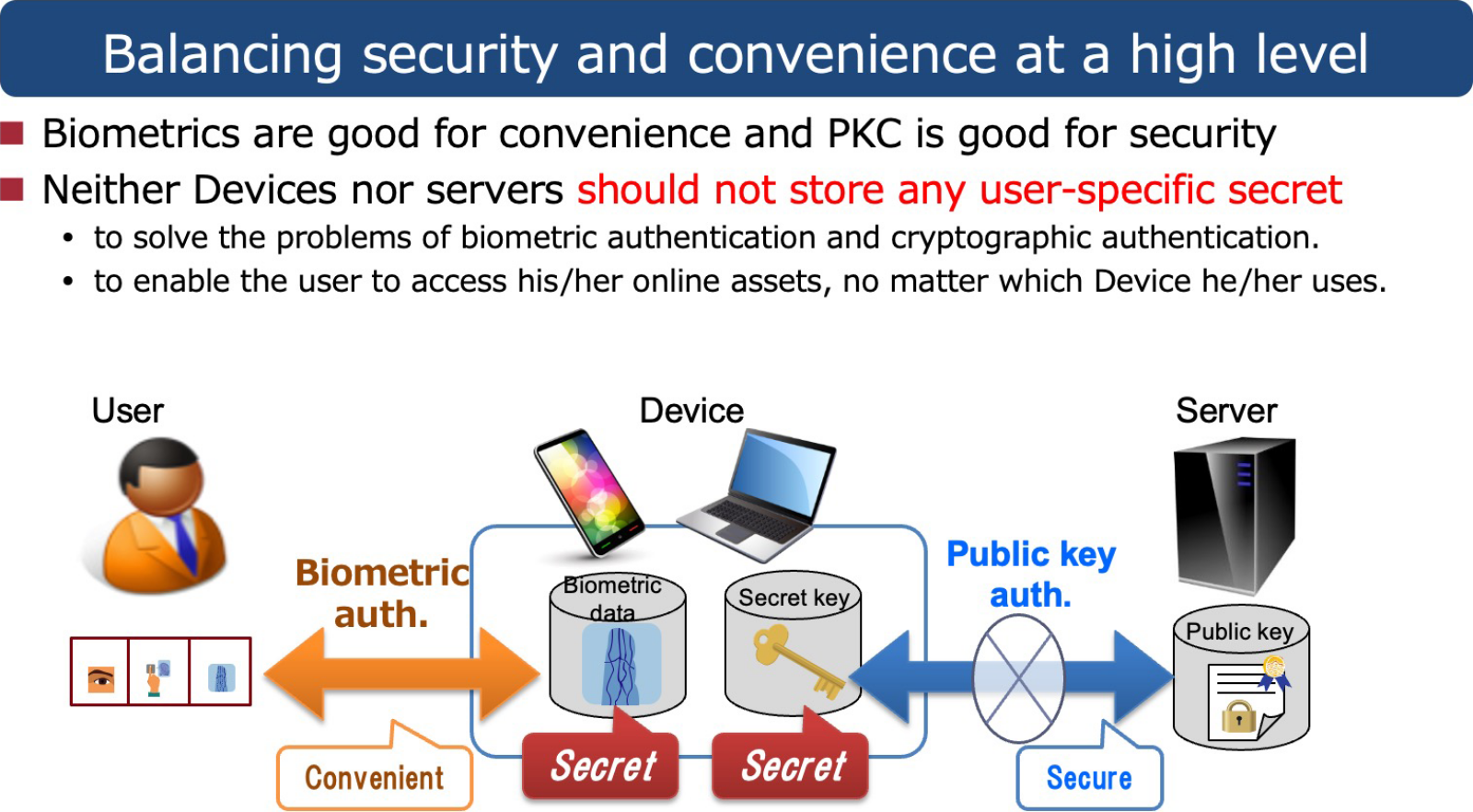
One solution to this problem is to eliminate the actual confidential authentication information which needs to be stored securely on a client device. If biometric authentication and public key authentication can be done without storing biometric data or private keys anywhere, a non-user-specific device could also be used to achieve empty-handed authentication. It would also allow users to immediately use services even after changing devices.
Let us now consider the best way to perform online authentication referring to the pros and cons of FIDO protocols. For user convenience and strict identity verification, biometric authentication (something you are) is preferable to other methods (something you know or have). However, the security and privacy of biometric data must be protected strictly. . At the same time, to reduce the risks related to managing personal information and cyber attacks on authentication systems, a strongly secure public key authentication protocol is preferable. Hitachi developed Public Biometric Infrastructure (PBI) as a technology capitalizing on the benefits of biometric and public key authentication without relying on user devices.
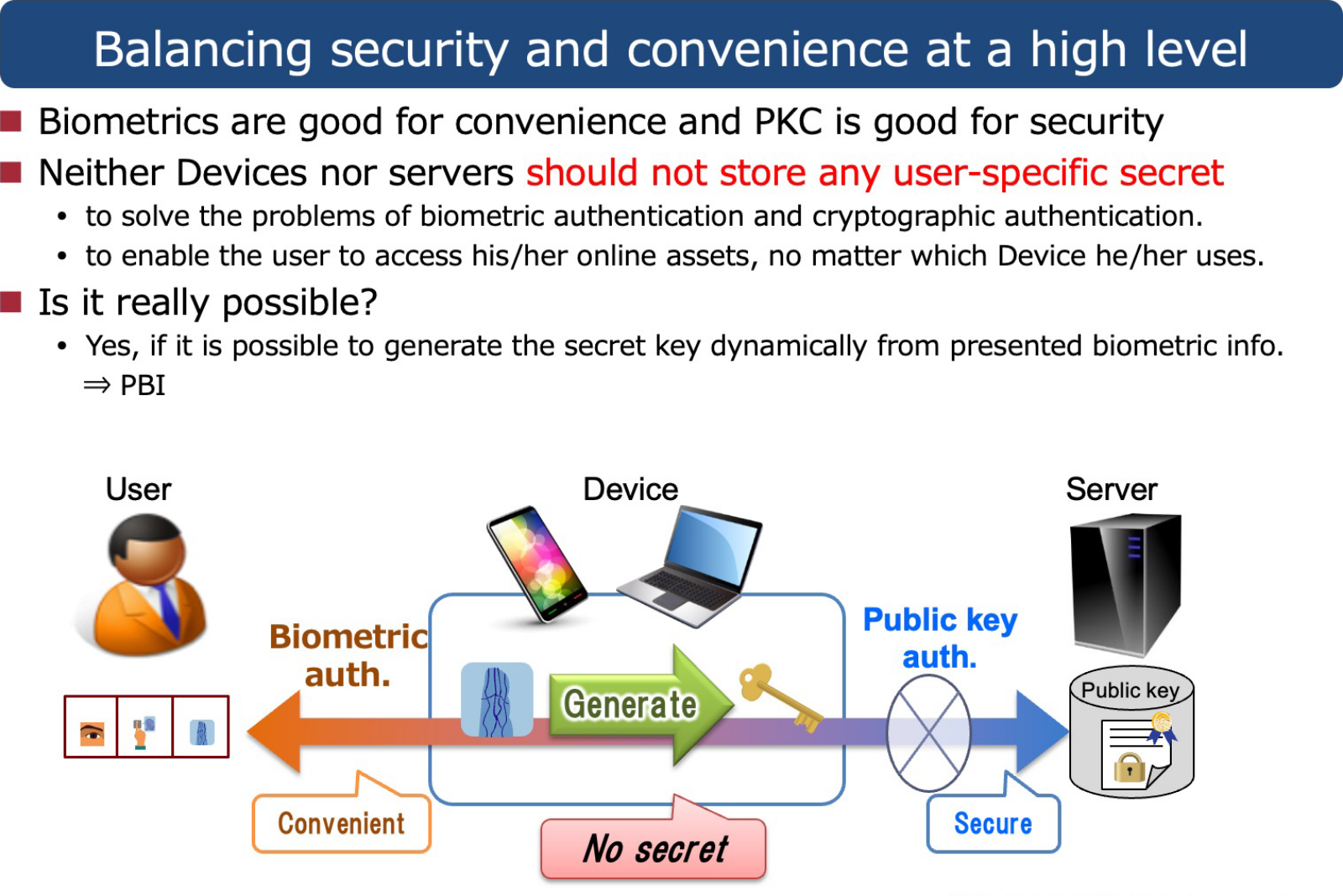
Put bluntly, a major difference between PBI and conventional authentication systems including biometric systems and Public Key Infrastructure (PKI) is that PBI no longer needs to store biometric data and private keys anywhere in the system in their raw form. This means that excessive management of private authentication information is no longer required for the authentication devices and servers, eliminating the Achilles’ heel of authentication. Specifically, an authentication device acquires biometric information from a user to generate a one-time private key to use in the PKI every time of authentication, instead of using a stored private key or stored biometric data. The device can then execute a public key authentication protocol with the server. The captured biometric data and generated private key are deleted immediately after authentication. This framework is the Public Biometric Infrastructure (PBI).
This is easier said than done. Making this idea a reality has been quite difficult. For starters, biometric information such as finger-vein patterns or facial features are originally analogue and fuzzy data that fluctuate even with the same user. In contrast a private key is digital data that cannot tolerate even a 1-bit error.. Generating digital private keys from fuzzy biometric data has been a challenging problem. We successfully developed PBI with two core technologies: fuzzy key generation and special error correction technology. Vein, facial, and other biometric information has a variety of fluctuating patterns. To minimize the range of these variations and stabilize the biometric feature data, we developed a method to extract feature vectors to limit errors within a small range in a special metric space for data from the same person, while keeping high diversity among feature vectors from different persons. The extracted feature vector to minimize errors is referred to as a fuzzy key. However, fuzzy keys still have some instability. Therein, fully correcting any remaining error consistently generates stable private keys. We developed technology that expanded theories of error correcting codes.
Hitachi first announced its development of basic PBI technology in 2013. Let’s review the various features of PBI. PBI can eliminate key management relying on smart devices, smart cards, passwords and similar authentication factors as well as realize digital authentication infrastructure that is able to verify the identity of a person while being user friendly at a low cost. At the time of registration, the user’s biometric information is mixed with a random string and converted to a PBI public key using one-way transformation, which makes it hard to recover the original biometric data or the private key . At the time of authentication the private key is re-generated temporarily from the user’s biometric information and used for the public key authentication protocol with the server. This minimizes the risk of a data leak because the original biometric data is not saved anywhere.
Leveraging these unique PBI properties, we successfully developed a biometric digital signature prototype system for electronic payments using finger vein authentication in 2014. In 2016, the Yamaguchi Financial Group made up of The Yamaguchi Bank, The Momiji Bank, and The Kitakyushu Bank started introducing a branch system that utilizes PBI. Customers can make deposits, withdrawals, and various other transactions on ATMs without a cash card by providing only an ID number and finger vein information for authentication. The branch system provides customers with convenient access to their money using only their fingers.
PBI can also be used for empty-handed payments at retail stores, such as supermarkets. We have not only demonstrated the validity of PBI at a real super market but also implemented a system that can process credit card payments using only a finger held out by customers at a Coffee shop in the Hitachi Yokohama Works. At a golf course in Chigasaki City, Kanagawa, Hitachi has also demonstrated the validity of a PBI concept that can check-in golfers and process payments using only a finger.
Hitachi launched a Biometrics Integrated Infrastructure Service in October 2020 to provide secure, user-friendly biometric PBI authentication for various services. As a cloud service, this easy-to-use authentication and digital signature system utilizing PBI is expected to broaden its use for a wide range of services from banking, cashless payments, and membership services to organizational ID management, telework, online healthcare, e-learning, and entry and exit management at various facilities.
We even announced a new biometric authentication device and other related technologies in March 2021 in light of the growing need for contactless biometric authentication to mitigate the risk of COVID-19 infections. One such device is the Hitachi Finger Vein Authentication Unit C-1, which is a contactless biometric device that can identify individuals by simply having them hold three fingers over a sensor. This new device can be used broadly at shops and other venues on a national scale because the system can support many millions of users. Hitachi also released the Hitachi Biometric SDK (Software Development Kit) for Windows, which allows standard cameras mounted on a general PC to be used as biometric authentication devices. Software developed using this kit eliminates the need for any special device by using only the computer camera to realize PBI biometric authentication. This innovation offers employees working remotely from home and other teleworkers easy yet secure personal authentication, whether logging into Windows, logging into company work systems using a single sign on, or even providing digital signatures.

Kenta TAKAHASHI
Principal Researcher, System Innovation Center, Hitachi Research and Development Group, and Ph.D. (Information Science and Technology)
Present research and development pertains to biometric authentication, cryptography, and information security
ISO/IEC SC37 expert and visiting Associate Professor at The University of Tokyo
The Ichimura Prize in Industry for Excellent Achievement (FY2020), R&D 100 Awards (2020), DOCOMO Mobile Science Advanced Technology Award of Excellence (2016), IPSJ Nagao Special Researcher Award (2014) and numerous other awards
I became fascinated by the fun and beauty of mathematics and theoretical physics as a junior high school student. I soon aspired to become a researcher while reading science magazines, journals, and textbooks. Einstein’s Theory of Relativity (Translated by: Ryoyu Uchiyama; Published by: Iwanami Bunko) made a particularly large impression on me when I read it in the first year of high school. The book is a Japanese translation of Zur Elektrodynamik bewegter Körper (On the Electrodynamics of Moving Bodies), the original paper on the Theory of Relativity published in 1905. The appearance of the Theory of Relativity completely transformed traditional physics, including the concepts of time and space. The first section, I. Kinematical Part, in this essay is said to contain the essence of it all. There are many different texts on the Theory of Relativity, but the original is without question the most interesting. I was astounded by the revolutionary change in thinking clearly abandoning convention as I read while imagining the historical backdrop. The beautiful logic unfolded simply but without any gaps in an almost literary type of storytelling. I hoped someday I would be able to write such a paper. Even today, I still hope I can.