![]()
The flow of packet data transmitted by typical worms
The following shows the typical five worms visualized by the tool.
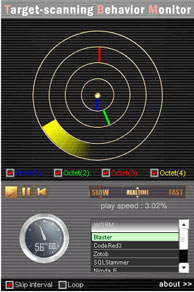
Blaster transmits a packet that attacks the vulnerability of Windows (MS03-026) to the TCP port #135*4 of random IP addresses.
Blaster searches IP addresses with a fixed 1st ~ 3rd octet and monotonically increases 4th octet. This will be because adjacent nodes in the same network segment as that of the infected node can be found effectively.
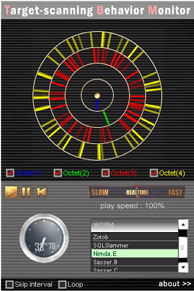
Nimda attacks vulnerability of the web server (IIS: Internet Information Service) (MS00-078) using TCP port #80 and transfers the body of the worm to the target node through TCP port #137 - #139 and #445.
Nimda expands the searching range by changing the 3rd ~ 4th octet randomly while fixing the 1st ~ 2nd octet of the destination IP address.
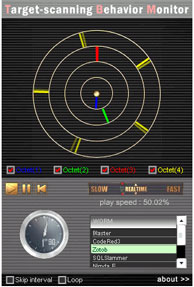
Zotob transmits packets that attack the vulnerability in Plug and Play of Windows (MS05-039) using TCP port #445.
Zotob searches IP addresses with fixed 1st ~ 3rd octet and regularly changes the 4th octet split in five blocks. Moreover, it gradually expands the search target over time, by gradually adding a random nature to the 3rd octet.
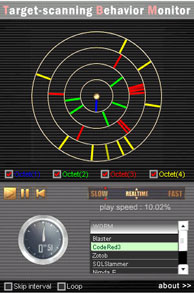
CodeRed transmits a packet that attacks the vulnerability of web server (IIS: Internet Information Service) (MS01-033) using TCP port #80.
CodeRed searches IP addresses changing the 2nd ~ 4th octet while fixing the 1st octet of the destination IP address. Moreover, it splits the 3rd octet into three blocks, which are regularly changed for searching, while also performing the same as the 4th octet.
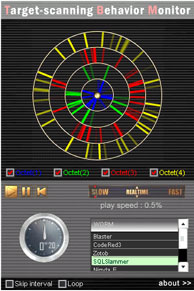
SQLSlammer targets the vulnerability of SQL Server 2000 (MS02-039) that transmits harmful packets to UDP port #1434.
SQLSlammer searches IP addresses by randomly changing the 1st ~ 4th octet of the destination IP address. This is intended to explore a wide range without limiting the target network.