![]()
Let's try the tool
You can see how worms change their behavior over time in more detail by visualizing them with the tool introduced on this site. Click the link below to try the tool..
You can view the visualized worms with basic operation only, but you can also change the settings. Please see the description of each function for details.
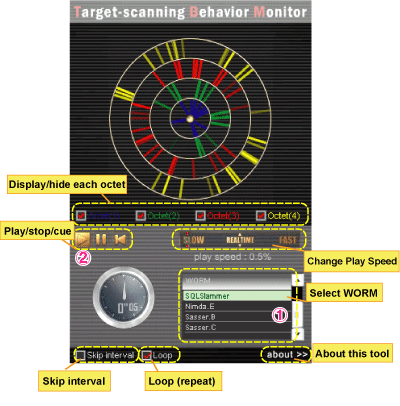
CodeRed3 |
Nimda E |
SQLSlammer |
Blaster |
Sasser B |
Sasser C |
Zotob |
Worm activity visualized by the tool above can be viewed in a movie as well. To view the movie, please download and unzip the files.
Visualization of each searching activity by worms enables you to visually check the characteristics of individual worm behavior. We believe quantified characteristics of the search activity can be used as information for detecting worm activities and identifying the type.
We will continue to challenge "viewing the invisible" by visualizing various security-related events from several perspectives and introducing our achievement on this site.
"Proposal for visualization of node searching characteristics of worm", written by Hirofumi Nakakoji, Masato Terada, Seiichi Susaki, Computer security research paper Vol. 2007 No. 036, Information Processing Society of Japan (Mar. 2007)
"Proposal for network worm behavior examination system" written by Masato Terada, Shingo Takada, Norihisa Doi, Information Processing Society of Japan Journal Vol. 46 No. 8, pp. 2014-2024 (2005)
Masato Terada, Shingo Takada, Norihisa Doi
Proposal for the experimental environment for Network Worm infection
17th Annual FIRST Conference (Shangri-La Hotel, Singapore, Jun.26 - Jul.1, 2005)
http://www.first.org/resources/papers/conf2005.html#p107
May. 10, 2007 - Add the videos.
Apr. 12, 2007 - This webpage was newly created and published.
Prepared by:
Nakakoji/Systems Development Laboratory, Terada/HIRT, Okashita/HIRT, Onishi/HIRT