Featured customer case
Lumada customer case code: UC-01724S
—Tokumei Bank: The Confidential Information Management Service—
2023-08-25

Is it possible to both protect personal information and also use it appropriately? This document explains how to do both. It introduces the service Tokumei Bank, which enables you to manage personal information by utilizing Hitachi’s proprietary anonymization technology. (In Japanese, Tokumei means anonymization.) This service, a Lumada initiative, enables organizations to handle personal information efficiently while using such information to provide more convenient products and services.
By using this service, organizations can:
Tokumei Bank can be used in a variety of operations and services, including centralized management of employee health information, registration of national ID numbers (such as Japan’s Individual Number, commonly referred to as My Number) at financial institutions, and enabling local governments to set up appointments for health checkups.
Hitachi will continue to expand the application of this service to different industries and fields so that organizations can protect personal information and use it appropriately, and the information providers (the persons providing their personal information) can eliminate their anxiety over how their information will be handled and can receive more convenient services.
Co‑creation with Lumada! Safe and centralized management of personal information
Careful consideration is required when handling personal information. However, the sharing and utilizing of such information can improve services and operational efficiency in various fields.
The use of cloud services has increased in recent years. As organizations (companies, local governments, medical institutions, etc.) move their IT infrastructure and services to the cloud, they are striving to improve operational efficiency and convenience by sharing and utilizing information.
Among the information held by such organizations, information such as the name, date of birth, or national ID number (such as Japan’s My Number) of the information provider are important data related to privacy, and must be handled in accordance with relevant laws, such as the country’s personal information protection laws and Europe’s General Data Protection Regulation (GDPR). The appropriate and effective use of personal information will lead to the provision of products and services that meet needs and preferences, and will enrich our lives and make them more comfortable. However, in a public opinion survey*1 conducted by Japan’s Cabinet Office, many respondents said they felt uneasy about how organizations were handling their personal information, so all such organizations must strive to eliminate the anxiety of information providers and earn their trust.
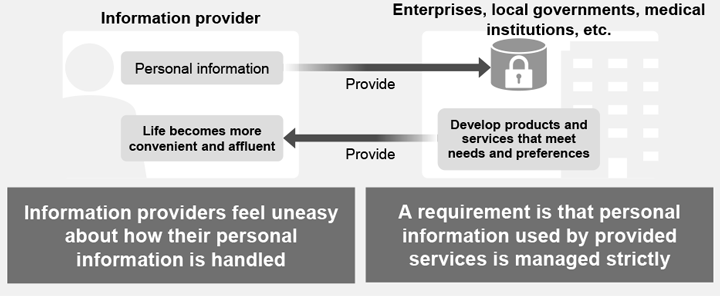
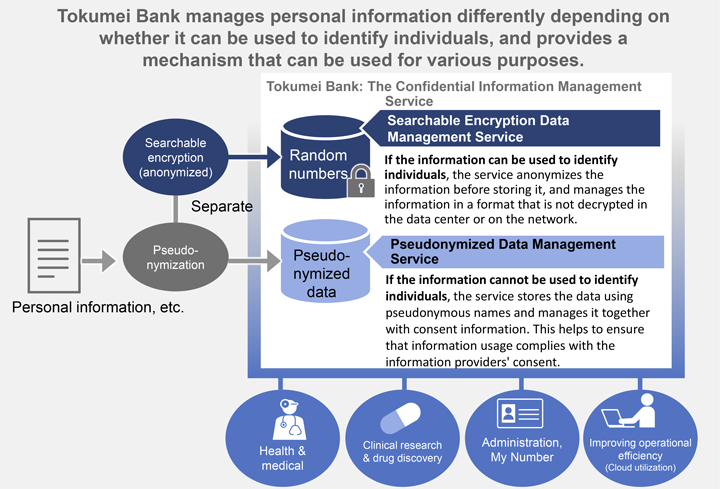
Advanced security technology is required to make the most of the usefulness of personal information while also protecting the rights and interests of the information providers. The Lumada solution, Tokumei Bank, uses Hitachi’s proprietary searchable encryption technology*2 to anonymize information that could be used to identify individuals. The technology provides a mechanism to safely manage data, which is replaced by random numbers in the cloud. Not decrypting the data in the data center or on the network during searches greatly reduces the risk of information leakage due to unauthorized access or internal crime.
In addition, information that cannot be used to identify individuals is pseudonymized and managed, which enables it to be used for various purposes within the scope of the consent provided by the information provider. This leads to more efficient personal‑information handling operations, reduces the cost of managing such information, and improves the convenience of end users by providing products and services that utilize their personal information.
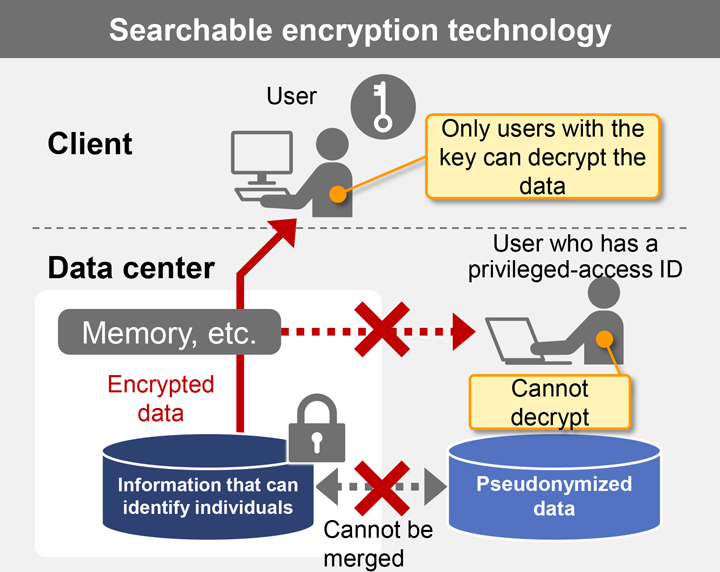
Formerly, when users searched encrypted data or used the data in calculations, traditional encryption required that the encrypted data be first decrypted in the data center. This process required that the decryption key be passed to the data center side, so that any user at the data center with a privileged‑access ID could decrypt the data. This entailed a risk of information leakage at the data center.
To remove this risk, searchable encryption technology, which provides a type of secure calculation processing, enables searches of data while the data remains encrypted. There is no need to pass the decryption key to the data center, so the risk of information leakage is reduced.
This technology ensures the following, so that organizations can use personal information as big data:
Tokumei Bank provides both secure data management in the cloud and also efficient operations using the data. The following page describes some features of Tokumei Bank and a case example.