With a shift to a zero-trust and internet-based architecture for IT infrastructure, the entire Hitachi Group will achieve a safe and secure IT environment for both its employees and businesses.
Business will expand through the introduction of new ways of working and the adoption of cloud services.
In the world of the internet, where cyberattacks are becoming increasingly sophisticated and skillful year after year, we are engaged in efforts to achieve safe and secure IT environments for both our employees and businesses throughout the entire Hitachi Group, in order to grow our businesses by introducing new ways of working and adopting cloud services.
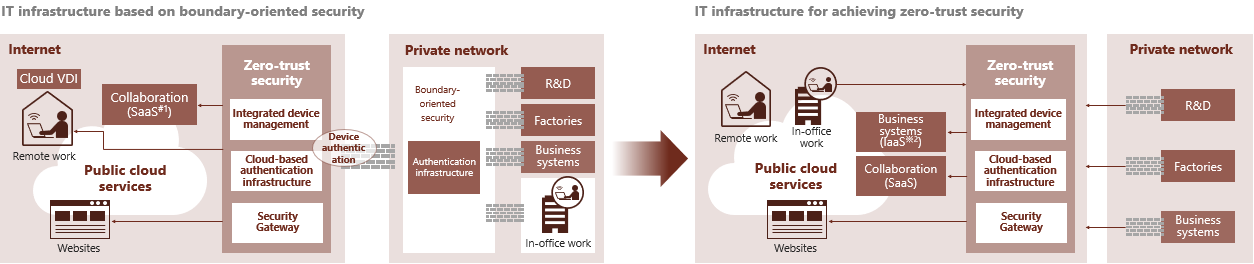
Following the steady entrenchment of hybrid work (office work and remote work) due to the spread of COVID-19, the Hitachi Group has been promoting a shift to an architecture based on zero-trust security to enable our employees to work securely anytime, anywhere.
Currently, we have completed shifting assets and services such as intranet sites and VDI to the cloud, and access control is performed through a cloud-based zero-trust security platform. In addition, we have finished segregating various on-premises systems within the private network, and are implementing access controls on differing network segments. Going forward, we will continue to promote the shift to direct internet connections for client devices, and further enhance our security measures.
The Hitachi Group is aiming for an environment that enables the seamless and safe use of information assets distributed on-premises and in the cloud by passing communications from client devices through a cloud-based zero-trust security platform.
Recently, we have introduced into our zero-trust security platform a device authentication function that controls access from unauthorized devices and an integrated device management function that audits PC and smartphone device posture and other information, thus strengthening the security of client devices that access information assets. In the future, we will promote functional enhancement of the zero-trust security platform and expand the fields to which it can be applied so that cloud services can be used safely even from plant, research, development, and other systems that are comprised mainly of on-premises environments.