Major platformers and specific powerful organizations collect, hold, and use personal data of individuals in ways unknown to those people. In a society which makes this possible, Hitachi Ltd. (Hereinafter “Hitachi”) is advancing the development of Public Biometric Infrastructure (PBI) technologies for the purpose of taking back our personal data sovereignty from major platformers and specific organizations as one of its goals. We sat down to talk with Principal Researcher Kenta Takahashi from the Research and Development Group about how Hitachi sees current and future biometric authentication and digital identity.
(March 25, 2022)Part 1 in this series presented the possibilities of using Public Biometric Infrastructure to balance security and user friendliness. The benefits included empty-handed payments and personal authentication as well as the use of a finger held up to a computer for system logins. However, this convenience is not our only goal. We aim to take back control of our digital identities. In other words, this is the approach to help realize a Self-Sovereign Identity (SSI) in which the individual has and controls their digital identity and personal data without all-powerful administrators acting as an intermediate.
As all of you know, a data economy is rapidly growing as a digital ecosystem. However, Google, Apple, Facebook, Amazon, Microsoft (GAFAM) and some other platformers as well as certain governments have the ability to collect and retain this data for economic and political gain. Without our knowledge, these organizations can track our actions, analyze and profile us using AI, and use our information to control our actions in ways that are beneficial for them. These platformers and governments currently control these huge amounts of personal data. Of course, there is also the perspective of the public good. This is the concept of giving up some rights to our data to public organizations even if we lose some privacy to prevent terror attacks or stop the COVID-19 pandemic. However, the United States, Europe, and other liberal nations are strengthening privacy laws and regulations by more strongly arguing the protection and privacy preservation of personal data is a fundamental human right and the data should be controlled by the individuals. Companies, governments, and individuals are three prominent entities beginning to engage in geopolitical tug of war over the right to control our personal data.
In the future, the rights to control digital identities and personal data will most likely be a fundamental right of the people. Companies and governments would need to gain the consent from every individual to use this data. With this belief, the Japanese government aims to realize Data Free Flow with Trust (DFFT). This framework seeks to enable the free flow of data while ensuring trust, and guaranteeing personal data sovereignty will surely become a major premise of trust.
The question then becomes how PBI will impact this issue of data sovereignty. One factor is authenticating the data owner. When personal data circulates with the consent of a person, biometric authentication can accurately and conveniently verify the person granting consent is actually the genuine one of that identity. During this process, PBI offers the unique ability for someone to manage their own biometric information, which is also personal data. Another factor is trust of consent. Companies would face serious risks and be unable to feel safe in using any data if the system cannot fully verify the person granting consent is really the individual with the right to control the data after distribution. PBI assigns a digital signature to consent form data using biometric information of the individual as a signing key to fully verify the consent even after the fact and after data distribution. The last factor is access control to personal data. Modern information management systems verify the identity of individuals upon entry, which leads to potential vulnerabilities. For example, a system administrator could easily access personal user data from a back door. PBI addresses this issue by creating an environment restricting data access to only the individual regardless of where people enter the system.
Let me explain this last aspect of access control in a bit more detail. PBI can be used for encryption in addition to authentication and digital signatures using biometric information. This means that you can encrypt your personal data with your biometric key. The encrypted data can be placed, for example, in a public cloud folder to allow access from anywhere. You are the only user who can generate the private key to recover the encrypted personal data even if leaked. Therefore, you can obtain an environment where only they have access to their personal data using PBI. It also lets users properly access personal data via physical traits without any personal device because PBI does not rely on smartphones or other devices someone has, or passwords or other things someone knows. This means end-to-end encryption which does not rely on terminals or devices makes it possible for users to freely store data anywhere they want safely.
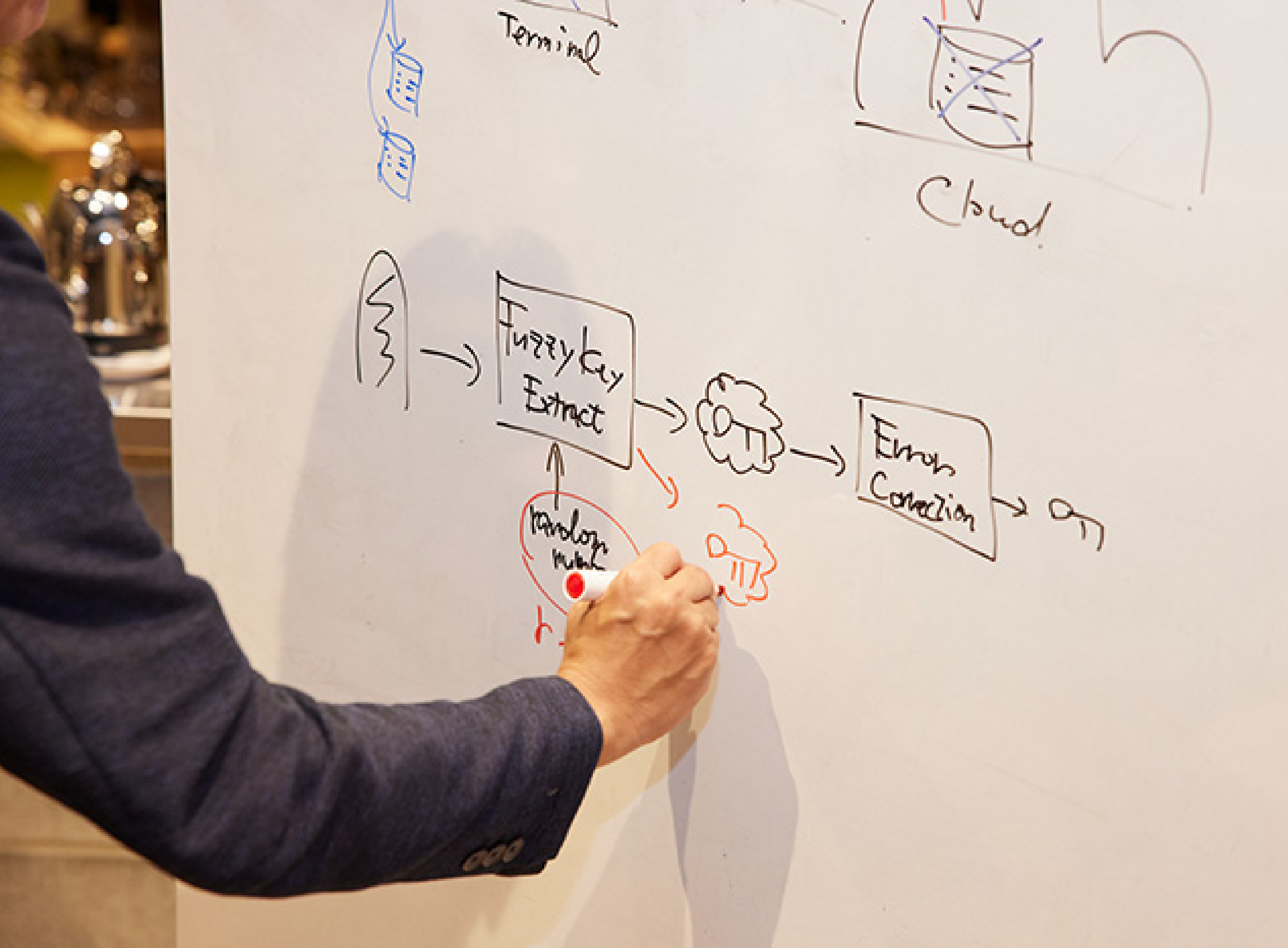
I think PBI can take back the self-sovereignty of our digital identities by building infrastructure that does not allow major platformers, governments, or anyone else to use personal data without the consent of individuals.
Hitachi is pioneering research and development into the new technologies necessary for individuals to use PBI for self-sovereign identity. One of these technologies is for selective disclosure. Personal data contains a variety of identity information and attributes of the person. Selective disclosure technologies let the users choose what to and not to disclose about themselves. This is a vital element to realize a self-sovereign identity, which is deeply tied to Decentralized Identity (DID) and Verifiable Credential (VC) concepts. An identity contains information such as nationality and other passport data as well as COVID-19 vaccination and PCR negative test certificates. Anyone traveling overseas may have to provide this type of information. For example, tourists at a bar may be asked to show their passports to buy alcohol. The passport not only shows the birth date of the person to prove they are of drinking age but also includes their nationality, name, address, and various other unnecessary information. A better approach would be to select only to disclose that you are of drinking age using trusted information that cannot be falsified.
Permanent data storage and tamper resistance are vital requirements for the realization of a Self-Sovereign Identity (SSI) and a Decentralized Identity (DID), which are highly compatible with blockchains. Let’s take a look at one use case. This is a use case for issuing a digital diploma and course records to certify someone has graduated from a university. A digital diploma issued using Public Key Infrastructure (PKI) may no longer be verifiable if the university closes and the public key is lost. This is not limited to diplomas. Any digital identity to verify something about someone needs to be permanently available.
This is an area where blockchain technologies are currently gleaning hope worldwide. By embedding a public key for the university in a blockchain, it should configure an environment that prevents the public key from being lost or overwritten and makes it permanently verifiable. Meanwhile, the use of cryptographic technologies including digital signatures on the block chain cause problems in managing private keys. The risk of cyber attacks or internal fraud, such as the outflow or compromise of a huge amount of cryptocurrencies or personal data, can be enormous at times, especially when storing the keys or data on central servers. From a self-sovereignty perspective in particular, it is important for users to manage their own data rather than leaving management up to a third party. That is why initiatives worldwide are working to make SSI a reality by managing private keys and digital identities using smartphones. However, this method can result in losing access to vital data if a smartphone is lost which would prevent someone from certifying their identity. People have in fact lost a device where a private key is stored and with it an enormous amount of cryptocurrency. The integration of PBI into the blockchain can overcome the challenges of managing private keys. This combination would help bring us even closer to a world that is able to shift the control of data from platformers to users.
Another consideration is the relationship with IoT required to create a human-centric, data-driven society. In the digital society to come, everything from automobiles and appliances to industrial equipment will connect to the internet, and systems will autonomously process and communicate data according to the intentions of administrators and owners. For example, small businesses and even a single person could trade renewable energy in real time. Each business and household system must not accidentally buy an excessive amount or sell off too much energy when autonomously trading renewable energy. Therefore, it is necessary to authenticate whether these sales and purchases adhere to the intentions of the individual owners and administrators. I think a technology to issue short-term device certificates based on PBI can be used to verify these intentions.
A short-term device certificate is data signed by an administrator or an owner based on PBI to prove that the device has been authorized for a period of time. For example, this certificate could contain a data set with information giving a device the authority to trade under certain requirements only for one day with a short-lived public key for that day. The device also contains a short-term private key corresponding to the public key and assigns digital signatures to trading data to send together with a short-term device certificate to the trading partner. This certificate can confirm the trade is not due to a malfunction or unauthorized use of device but an actual trade reflecting the intentions of the real administrator. Even in the IoT era, the origin of trust for transactions and data distribution will surely always remain human. People and administrators will always be accountable and responsible for any trouble or accidents even if caused by machines. To certify this accountability and responsibility, I think PBI can act as an essential technology.
As smartphones become more prevalent, one main point when talking about the future form of PBI is the risk of putting everything on a single device as private authentication information for self-sovereignty in a digital society, whether financial assets, payments, or various service accounts. In addition, our digital identity to prove who we are in society is also being integrated into smartphones. Even if these smartphones become wearable devices in the future, we would still rely on something we have. This something then becomes who we are in the digital world, which creates a place in which the moment this something is lost is the moment we lose who we are.
Progress in digitalization has rung in an era quickly accumulating a life log and other personal data about us. That is why I believe it will become important to guarantee our identity is tied to our physical body rather than something we have. The next important step is to provide a technical means to ensure data sovereignty which guarantees protection, selective disclosure and proof of authenticity of personal data based on the person’s own consent. Someone generally does not need to disclose a life log about a lot hard work in high school baseball with the hope of playing in the championships, but it could be advantageous to have the self-sovereignty to disclose such information when job hunting or in other special circumstances.
Presently, a lot of personal information is collected in the cloud by platformers like GAFAM through various services, applications and browsers. Engineers around the world are working very hard to build a framework to bring that personal data to smartphones and other personal devices so that users can have the self-sovereignty to manage that data themselves. Even if these engineers are successful, anyone who lost their devices would be unable to verify their identity and in turn lose their virtual selves in the digital space. This should not happen. By virtually tying digital identities to our physical selves rather than to a device, PBI can verify the identity of a person with only their physical traits. I think this is one of the most significant aspects of PBI.

Of course, I do not think simply overcoming the technical challenges will make PBI a worldwide phenomenon. The ecosystem is especially important from a business standpoint and something Hitachi cannot build alone. It is important to forge partnerships, standardize the infrastructure, and build a business ecosystem. I have talked with many different people about PBI. Everyone says they like the idea and empathizes with this ideal form of society.
We are finally at a stage of research and development as well as business promotion to introduce PBI into society. Designers from the Center for Global Social Innovation are also participating in this project. We will continue putting all of our effort into pioneering PBI together with our partners while continuing discussions with people both inside and outside of Hitachi. Research and development that anticipates future social issues is not compatible with a type of business that focuses on short-term benefits. This makes it difficult at times to form collaborative relationships. I hope we can be patient as we build relationships to drive forward together as partners toward this ideal society.

Kenta TAKAHASHI
Principal Researcher, System Innovation Center, Hitachi Research and Development Group, and Ph.D. (Information Science and Technology)
Present research and development pertains to biometric authentication, cryptography, and information security
ISO/IEC SC37 expert and visiting Associate Professor at The University of Tokyo
The Ichimura Prize in Industry for Excellent Achievement (FY2020), R&D 100 Awards (2020), DOCOMO Mobile Science Advanced Technology Award of Excellence (2016), IPSJ Nagao Special Researcher Award (2014) and numerous other awards
I became fascinated by the fun and beauty of mathematics and theoretical physics as a junior high school student. I soon aspired to become a researcher while reading science magazines, journals, and textbooks. Einstein’s Theory of Relativity (Translated by: Ryoyu Uchiyama; Published by: Iwanami Bunko) made a particularly large impression on me when I read it in the first year of high school. The book is a Japanese translation of Zur Elektrodynamik bewegter Körper (On the Electrodynamics of Moving Bodies), the original paper on the Theory of Relativity published in 1905. The appearance of the Theory of Relativity completely transformed traditional physics, including the concepts of time and space. The first section, I. Kinematical Part, in this essay is said to contain the essence of it all. There are many different texts on the Theory of Relativity, but the original is without question the most interesting. I was astounded by the revolutionary change in thinking clearly abandoning convention as I read while imagining the historical backdrop. The beautiful logic unfolded simply but without any gaps in an almost literary type of storytelling. I hoped someday I would be able to write such a paper. Even today, I still hope I can.